1. Introduction & Overview
What is a FinOps Practitioner?
A FinOps Practitioner is a professional skilled in Cloud Financial Operations (FinOps), a discipline that integrates financial accountability into cloud management to optimize costs while maintaining performance and agility. FinOps Practitioners bridge finance, engineering, and business teams to ensure cloud investments align with organizational goals. They leverage data-driven insights, cost allocation strategies, and automation to manage cloud spending effectively.
History or Background
FinOps emerged as cloud adoption surged, driven by the need to control variable cloud costs. The FinOps Foundation, established under the Linux Foundation, formalized the practice in 2019, providing frameworks, certifications, and community resources. The FinOps Certified Practitioner (FOCP) certification, launched in 2021, validates expertise in cloud cost management. As organizations adopted DevOps and DevSecOps, FinOps became critical to integrate financial oversight into rapid development cycles.
Why is it Relevant in DevSecOps?
In DevSecOps, which embeds security into the DevOps lifecycle, managing cloud costs is crucial as teams deploy and scale applications rapidly. FinOps Practitioners ensure that security and operational decisions don’t lead to cost overruns, aligning with DevSecOps’ focus on speed, security, and efficiency. They enable cross-functional collaboration, ensuring cloud resources are optimized without compromising security or performance.
- Cost Accountability: Ensures DevSecOps teams understand the financial impact of their deployments.
- Security Integration: Balances security tool costs with budget constraints.
- Scalability: Supports rapid scaling while maintaining cost efficiency.
2. Core Concepts & Terminology
Key Terms and Definitions
- FinOps: A cultural and operational framework for managing cloud costs through collaboration between finance, engineering, and business teams.
- FinOps Practitioner: A certified professional who implements FinOps principles, often using tools like AWS Cost Explorer, Azure Cost Management, or Google Cloud Billing.
- FOCUS: FinOps Open Cost and Usage Specification, a standardized format for cloud billing data.
- Cost Allocation: Assigning cloud costs to specific teams, projects, or workloads using tags or labels.
- Inform, Optimize, Operate: The three phases of the FinOps lifecycle, focusing on visibility, cost optimization, and continuous management.
| Term | Definition |
|---|---|
| FinOps | A cultural practice that combines financial accountability with cloud operations. |
| Showback/Chargeback | Visibility (showback) or billing (chargeback) of cloud costs to respective teams. |
| Unit Economics | Cost per customer or per unit of value (e.g., per API call or deployment). |
| Cloud Cost Allocation | Assigning cloud spend to services, teams, or cost centers. |
| Optimization | Continuous rightsizing and scheduling to reduce cloud waste. |
| Cost Anomaly Detection | Identifying unusual spikes or dips in cloud spend. |
How It Fits into the DevSecOps Lifecycle
DevSecOps integrates development, security, and operations into a continuous cycle (Plan, Code, Build, Test, Release, Deploy, Operate, Monitor). FinOps Practitioners contribute at each stage:
- Plan/Code: Forecast costs for new features or security tools.
- Build/Test: Monitor costs of CI/CD pipelines and testing environments.
- Deploy/Operate: Optimize resource usage (e.g., shutting down unused instances).
- Monitor: Use cost analytics to track spending and identify anomalies.
graph LR
A[Plan] --> B[Develop]
B --> C[Test]
C --> D[Secure]
D --> E[Deploy]
E --> F[Monitor]
F --> G[Optimize Costs (FinOps)]
G --> A
By embedding financial accountability, FinOps ensures DevSecOps teams balance speed, security, and cost.
3. Architecture & How It Works
Components and Internal Workflow
A FinOps Practitioner’s workflow involves:
- Data Collection: Gathering cloud usage and cost data from providers (e.g., AWS, Azure, GCP).
- Cost Allocation: Using tags/labels to assign costs to teams or projects.
- Analysis and Reporting: Generating insights via tools like CloudZero or native cloud consoles.
- Optimization: Recommending actions like rightsizing instances or leveraging commitment discounts.
- Automation: Implementing policies to manage costs (e.g., auto-scaling, shutdown scripts).
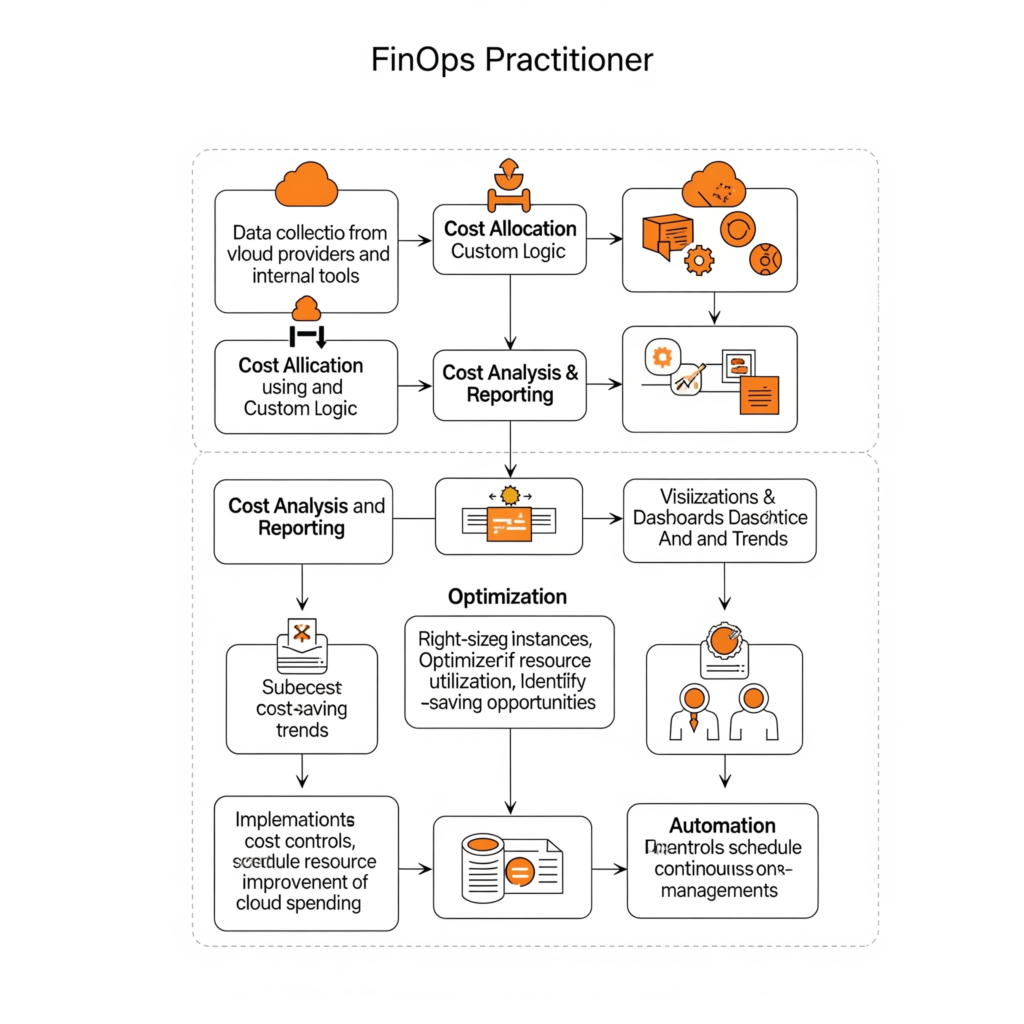
Architecture Diagram Description
Imagine a layered architecture:
- Top Layer (Cloud Provider): AWS, Azure, or GCP provides raw billing data.
- Middle Layer (FinOps Tools): Tools like CloudZero, AWS Cost Explorer, or Apptio Cloudability process data, apply tags, and generate reports.
- Bottom Layer (DevSecOps Pipeline): CI/CD tools (e.g., Jenkins, GitLab) integrate with FinOps tools to monitor pipeline costs.
- Cross-Layer (FinOps Practitioner): Acts as the orchestrator, analyzing data, setting policies, and collaborating with teams.
+-------------------------+
| Cloud Providers (AWS) |
+-----------+-------------+
|
Cost & Usage Data
↓
+---------------------------+
| FinOps Data Pipeline |
| - Data Collectors |
| - Normalization Engine |
| - Anomaly Detection |
+---------------------------+
↓
+---------------------------+
| Dashboards & Alerts |
| - Tag-based Reports |
| - Team Spend Reports |
| - Optimization Insights |
+---------------------------+
↓
+---------------------------+
| Automation & CI/CD Tools |
| - Slack alerts |
| - Terraform cost modules |
| - GitHub/GitLab actions |
+---------------------------+
Integration Points with CI/CD or Cloud Tools
- CI/CD Integration: FinOps tools can integrate with Jenkins or GitLab to monitor pipeline resource usage. For example, a script can alert teams if a test environment exceeds budget.
- Cloud Tools: Native tools like AWS Budgets or Azure Cost Management provide real-time cost alerts. Third-party tools like Harness integrate cost data into DevSecOps dashboards.
# Example: AWS CLI command to set a budget alert
aws budgets create-budget \
--account-id 123456789012 \
--budget-name MyDevSecOpsBudget \
--budget-type COST \
--budget-limit '{"Amount": 1000, "Unit": "USD"}' \
--time-unit MONTHLY \
--notifications '{"NotificationType": "ACTUAL", "Threshold": 80, "ComparisonOperator": "GREATER_THAN"}'
| Tool | Integration Use Case |
|---|---|
| Terraform | Use cost-estimation tools like infracost during PRs. |
| GitHub Actions | Post spend reports as part of CI pipelines. |
| Prometheus/Grafana | Visualize spend per microservice using custom exporters. |
| AWS Budgets | Trigger Lambda functions on budget breaches. |
4. Installation & Getting Started
Basic Setup or Prerequisites
- Knowledge: Basic understanding of cloud platforms (AWS, Azure, GCP) and DevSecOps principles.
- Tools: Access to cloud provider consoles, FinOps tools (e.g., CloudZero, Apptio), and CI/CD platforms (e.g., Jenkins).
- Certifications: Optional FinOps Certified Practitioner (FOCP) certification for structured learning.
- Permissions: IAM roles for accessing billing data (e.g., AWS Billing and Cost Management).
Hands-On: Step-by-Step Beginner-Friendly Setup Guide
- Set Up Cloud Billing Access:
- Log into AWS Management Console.
- Navigate to “Billing and Cost Management.”
- Enable Cost Explorer and activate cost allocation tags.
- Enable Tagging:
- Define tags (e.g.,
Environment: Dev,Team: Security) in the cloud provider’s tagging editor. - Apply tags to resources like EC2 instances or Kubernetes clusters.
- Define tags (e.g.,
- Integrate a FinOps Tool:
- Sign up for CloudZero or Apptio Cloudability.
- Connect the tool to your cloud provider via API keys.
- Configure dashboards to visualize costs by team or project.
- Set Up Budget Alerts:
- Use the AWS CLI command above to create a budget.
- Configure notifications via SNS or email for cost thresholds.
- Integrate with CI/CD:
- Add a cost monitoring step in your Jenkins pipeline:
# Jenkins pipeline snippet to check AWS costs
stage('Check Costs') {
steps {
sh 'aws ce get-cost-and-usage --time-period Start=$(date -u +%Y-%m-01),End=$(date -u +%Y-%m-%d) --granularity MONTHLY --metrics "UnblendedCost"'
}
}
- Test and Validate:
- Run a pipeline and verify cost data in the FinOps tool.
- Adjust tags or budgets based on insights.
5. Real-World Use Cases
Scenario 1: Optimizing CI/CD Pipeline Costs
A DevSecOps team uses Jenkins for CI/CD. A FinOps Practitioner identifies that test environments are left running, costing $500/month. They implement an auto-shutdown policy for idle instances, reducing costs by 40%.
Scenario 2: Security Tool Cost Management
A financial services company deploys a security scanning tool in Azure. The Practitioner uses cost allocation tags to track tool usage, identifying overprovisioned resources and saving 20% by rightsizing.
Scenario 3: Kubernetes Cost Allocation
A SaaS company runs Kubernetes clusters on GCP. The Practitioner integrates KubeCost to allocate costs by namespace, enabling the security team to optimize container security tools without exceeding budgets.
Scenario 4: Public Sector Compliance
A government agency adopting DevSecOps uses FinOps to ensure cloud spending complies with budgetary regulations. The Practitioner forecasts costs for a new security compliance tool, ensuring alignment with federal guidelines.
6. Benefits & Limitations
Key Advantages
- Cost Optimization: Reduces cloud spend by identifying waste (e.g., unused instances).
- Collaboration: Bridges finance, engineering, and security teams.
- Scalability: Supports rapid DevSecOps scaling with cost control.
- Transparency: Provides visibility into cloud costs via tagging and reporting.
Common Challenges or Limitations
- Complexity: Managing tags across large organizations can be cumbersome.
- Tool Dependency: Relies on third-party or native tools, which may have learning curves.
- Cultural Resistance: Teams may resist cost accountability in fast-paced DevSecOps environments.
- Data Accuracy: Inconsistent tagging can lead to inaccurate cost allocation.
7. Best Practices & Recommendations
Security Tips
- Secure Billing Access: Restrict billing data access to authorized roles (e.g., AWS IAM policies).
- Monitor Anomalies: Use tools like AWS Cost Anomaly Detection to flag unusual spending, which could indicate security breaches.
Performance
- Automate Tagging: Use Infrastructure-as-Code (IaC) to enforce consistent tagging:
# Terraform example for AWS resource tagging
resource "aws_instance" "example" {
ami = "ami-12345678"
instance_type = "t2.micro"
tags = {
Environment = "Dev"
Team = "Security"
}
}
- Rightsize Resources: Regularly analyze usage to downsize overprovisioned instances.
Maintenance
- Regular Audits: Conduct monthly cost reviews to identify optimization opportunities.
- Update Policies: Adjust budgets and alerts based on project changes.
Compliance Alignment
- Align with frameworks like NIST or SOC 2 by documenting cost allocation processes.
- Use FOCUS-compliant billing data for standardized reporting across clouds.
Automation Ideas
- Automate shutdown of non-production environments using AWS Lambda or Azure Functions.
- Integrate cost alerts into Slack or Teams for real-time notifications.
8. Comparison with Alternatives
| Aspect | FinOps Practitioner | Traditional IT Finance | DevOps Cost Monitoring |
|---|---|---|---|
| Focus | Cloud cost optimization, collaboration | Budget tracking, fixed IT costs | Ad-hoc cost monitoring in pipelines |
| Tools | CloudZero, AWS Cost Explorer, KubeCost | Spreadsheets, ERP systems | Native cloud tools, limited scope |
| Collaboration | Cross-functional (finance, engineering) | Finance-centric | Engineering-centric |
| Security Integration | Balances security tool costs | Limited security focus | Security often secondary |
| When to Choose | Dynamic cloud environments, DevSecOps | Static on-premises IT | Basic pipeline cost tracking |
When to Choose FinOps Practitioner:
- Use in cloud-heavy DevSecOps environments requiring cost, security, and performance balance.
- Avoid for small-scale projects with minimal cloud usage, where native tools suffice.
9. Conclusion
FinOps Practitioners play a pivotal role in DevSecOps by embedding financial accountability into the development lifecycle. They enable teams to innovate rapidly while controlling costs and maintaining security. As cloud adoption grows, the role will evolve with AI-driven cost analytics and advanced automation. To get started, explore the FinOps Foundation’s resources or pursue the FOCP certification.