1. Introduction & Overview
What is DevSecOps in Financial Services?
DevSecOps in Financial Services refers to the integration of security practices into the DevOps pipeline, tailored for the unique needs of financial institutions. It combines Development, Security, and Operations to ensure that financial applications—handling sensitive data like personal and financial information—are developed, deployed, and maintained securely, efficiently, and in compliance with strict regulations. This approach embeds security at every stage of the software development lifecycle (SDLC), from planning to deployment, to mitigate risks in a highly regulated and cyber-threat-prone industry.
History or Background
The term DevSecOps emerged as an evolution of DevOps, which focused on collaboration between development and operations teams to accelerate software delivery. In the financial sector, the rise of digital banking, fintech, and mobile-first applications (post-2010) exposed new vulnerabilities, necessitating a security-first approach. The 2010s saw increased cyberattacks on financial institutions, with breaches costing an average of $5.86 million per incident (). Regulatory frameworks like PCI DSS, GDPR, and MiFID further drove the adoption of DevSecOps to ensure compliance and protect sensitive data. By 2020, financial services were among the leaders in DevOps maturity, with DevSecOps becoming critical to address security at the “grass-root level” ().
Why is it Relevant in DevSecOps?
- High Stakes: Financial applications handle sensitive data, making them prime targets for cyberattacks (e.g., 62% of financial apps faced attacks in a 4-week period in 2023) ().
- Regulatory Compliance: Regulations like PCI DSS and Strong Customer Authentication (SCA) require robust security and auditability ().
- Speed and Security: DevSecOps balances rapid deployment with security, crucial for fintech’s competitive, fast-paced market ().
- Customer Trust: A single breach can erode trust, leading to customer loss and reputational damage ().
2. Core Concepts & Terminology
Key Terms and Definitions
- DevSecOps: A methodology integrating security into the DevOps pipeline, emphasizing automation, collaboration, and continuous security.
- Shift-Left Security: Incorporating security practices early in the SDLC to identify vulnerabilities before deployment ().
- Infrastructure as Code (IaC): Managing infrastructure through code to enable automation and consistency ().
- Continuous Integration/Continuous Deployment (CI/CD): Automated processes for building, testing, and deploying code.
- Static Application Security Testing (SAST): Analyzes source code for vulnerabilities without execution ().
- Dynamic Application Security Testing (DAST): Tests running applications for vulnerabilities ().
- Interactive Application Security Testing (IAST): Combines SAST and DAST using agents for real-time vulnerability detection ().
- Software Bill of Materials (SBOM): A list of software components to track dependencies and vulnerabilities
| Term | Definition |
|---|---|
| Unit Economics | Financial measure that evaluates revenue and cost per unit of output |
| Showback/Chargeback | Cost allocation methods for internal billing across departments |
| Cloud FinOps | Financial Operations practice for cloud optimization |
| Tagging Strategy | Metadata labeling of resources for financial visibility and governance |
| Cost Anomaly Detection | Automated alerting on unexpected cloud spend |
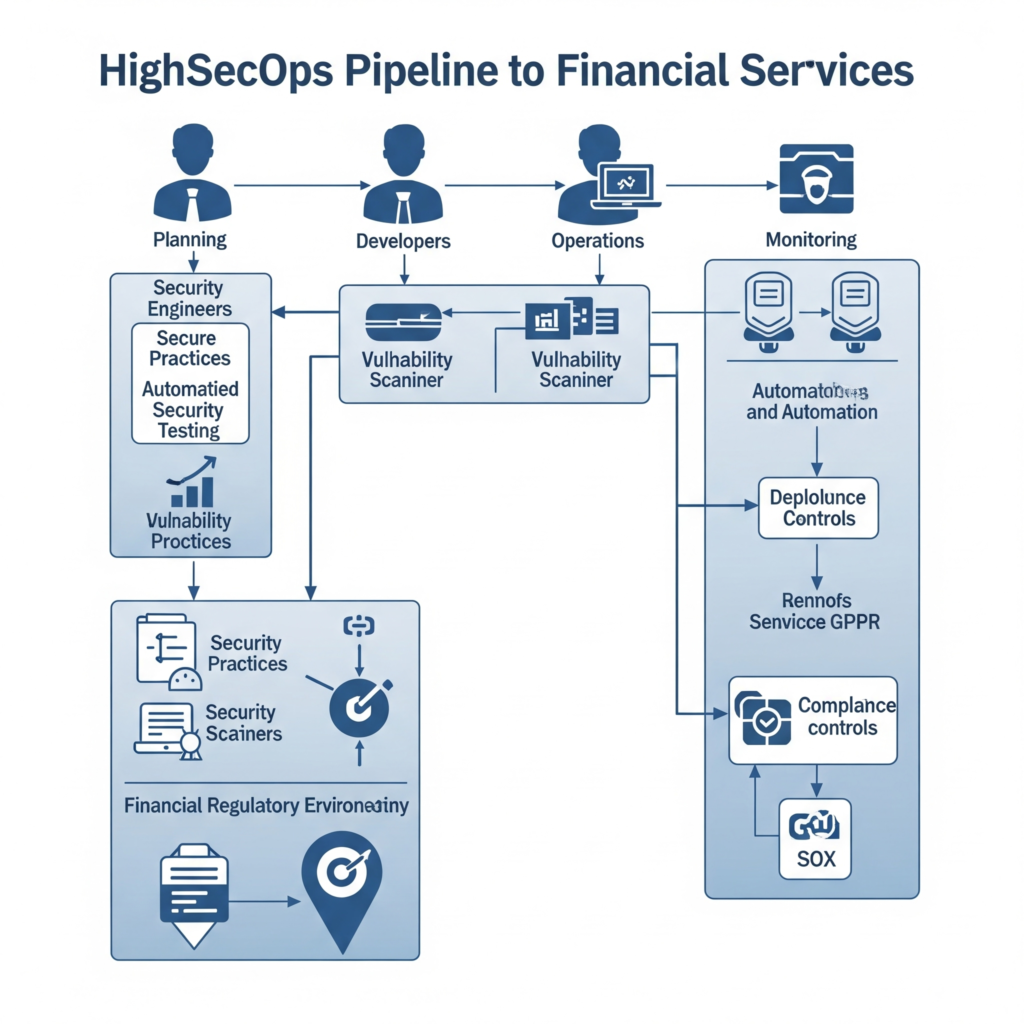
How It Fits into the DevSecOps Lifecycle
DevSecOps in finance integrates security into the following SDLC phases:
- Plan: Threat modeling and compliance requirements are defined.
- Code: Secure coding practices and SAST tools scan code for vulnerabilities.
- Build: Automated security checks in CI pipelines (e.g., dependency scanning).
- Test: DAST and IAST tools test applications in staging environments.
- Deploy: IaC ensures secure infrastructure deployment.
- Monitor: Continuous monitoring for threats and compliance (e.g., SIEM solutions) ().
This lifecycle ensures security is not an afterthought but a continuous process, critical for financial applications.
| DevSecOps Stage | Finance Partner Involvement |
|---|---|
| Plan | Budget planning, cost-benefit analysis for security tools |
| Develop | Cost implications of licensing, open-source trade-offs |
| Build | Integrating cost controls into CI/CD pipelines |
| Test | Budget for dynamic testing tools (e.g., DAST, SAST licenses) |
| Release | Ensuring cost efficiency in release pipelines |
| Operate | Ongoing cost governance, anomaly detection, cost alerts |
| Monitor | Real-time dashboards of cost performance and KPIs |
3. Architecture & How It Works
Components
- Version Control System (VCS): Tools like Git manage code and IaC ().
- CI/CD Pipeline: Tools like Jenkins, GitLab CI, or Bitrise automate builds, tests, and deployments ().
- Security Tools: SAST (e.g., SonarQube), DAST (e.g., OWASP ZAP), IAST (e.g., Contrast Security), and secret management (e.g., AWS Secrets Manager) (,).
- Monitoring Tools: SIEM solutions and logging for real-time threat detection ().
- Compliance Frameworks: Tools to enforce PCI DSS, GDPR, etc.
Internal Workflow
- Code Commit: Developers push code to a VCS, triggering CI/CD pipelines.
- Automated Testing: SAST scans for code vulnerabilities; DAST tests running apps.
- Dependency Scanning: Tools like Snyk check for vulnerabilities in open-source libraries ().
- Infrastructure Deployment: IaC tools (e.g., Terraform) deploy secure environments.
- Continuous Monitoring: SIEM tools detect anomalies post-deployment.
Architecture Diagram Description
Imagine a pipeline diagram:
- Input: Code and IaC in Git.
- CI/CD Stages: Build (Jenkins), Test (SAST/DAST), Deploy (Terraform), Monitor (SIEM).
- Security Layer: Integrated at each stage with tools like Snyk, OWASP ZAP, and AWS Secrets Manager.
- Feedback Loop: Monitoring feeds back to developers for remediation.
+----------------+ +--------------------+ +------------------+
| Cloud Provider | -> | Cost Data Collector| -> | Analytics & BI |
+----------------+ +--------------------+ +------------------+
^ | |
| v v
+----------------+ +-------------------+ +------------------+
| DevSecOps Tool | -> | Tagging & Metadata| <--> | Governance Engine|
+----------------+ +-------------------+ +------------------+
Integration Points with CI/CD or Cloud Tools
- CI/CD: Jenkins or GitLab CI integrates SAST/DAST tools via plugins.
- Cloud: AWS Secrets Manager for secure key management; AWS CloudFormation for IaC ().
- Third-Party: Snyk for dependency scanning, Data Theorem for mobile app security ().
4. Installation & Getting Started
Basic Setup or Prerequisites
- Tools Needed: Git, Jenkins, Terraform, Snyk, OWASP ZAP, AWS account.
- Environment: Linux/Windows server or cloud instance (e.g., AWS EC2).
- Skills: Basic knowledge of Git, CI/CD, and cloud concepts.
Hands-On: Step-by-Step Setup Guide
- Set Up Git Repository:
git init finance-app
cd finance-app
git commit -m "Initial commit"2. Install Jenkins:
- Download Jenkins (https://www.jenkins.io/download/).
- Run:
java -jar jenkins.war --httpPort=8080. - Access at
http://localhost:8080and configure.
3. Configure Snyk for Dependency Scanning:
- Sign up at https://snyk.io.
- Install Snyk CLI:
npm install -g snyk. - Authenticate:
snyk auth. - Scan:
snyk test.
4. Set Up OWASP ZAP for DAST:
- Download OWASP ZAP (https://www.zaproxy.org/download/).
- Run:
./zap.sh(Linux) orzap.bat(Windows). - Configure automated scans in Jenkins pipeline.
5. Deploy IaC with Terraform:
- Install Terraform (https://www.terraform.io/downloads.html).
- Create
main.tf:
provider "aws" {
region = "us-east-1"
}
resource "aws_instance" "app" {
ami = "ami-12345678"
instance_type = "t2.micro"
}Run: terraform init && terraform apply.
6. Monitor with AWS CloudWatch:
- Enable CloudWatch in AWS Console.
- Set up logs and alerts for application monitoring.
5. Real-World Use Cases
- Mobile Banking App Security:
- Trading Platform Compliance:
- Fraud Detection System:
- API Security for Payment Gateway:
6. Benefits & Limitations
Key Advantages
- Enhanced Security: Shift-left security reduces vulnerabilities early ().
- Compliance: Automated checks ensure adherence to PCI DSS, GDPR, etc. ().
- Faster Delivery: Automation speeds up secure releases ().
- Collaboration: Breaks silos between dev, sec, and ops teams ().
Common Challenges or Limitations
- Complexity: Managing multiple tools (SAST, DAST, IAST) can be overwhelming ().
- False Positives/Negatives: SAST/DAST tools may miss unknown threats or flag non-issues ().
- Skill Gap: Requires expertise in security and DevOps ().
- Cost: Initial setup and tool licensing can be expensive.
7. Best Practices & Recommendations
- Security Tips:
- Performance:
- Maintenance:
- Compliance Alignment:
- Automation Ideas:
8. Comparison with Alternatives
| Feature | DevSecOps (Financial) | Traditional AppSec | DevOps (No Security) |
|---|---|---|---|
| Security Integration | Embedded in SDLC | Post-development | Minimal or none |
| Automation | High (SAST, DAST, IAST) | Limited | High (CI/CD only) |
| Compliance | Built-in checks | Manual audits | Not prioritized |
| Speed | Fast with security | Slow due to manual | Fast but risky |
| Cost | High initial, long-term savings | High long-term | Lower initial, high risk |
When to Choose DevSecOps
- Choose DevSecOps for financial applications requiring high security and compliance (e.g., banking, fintech).
- Opt for traditional AppSec for less regulated, low-risk projects.
- Avoid DevOps without security for sensitive data applications due to high breach risks ().
9. Conclusion
DevSecOps in Financial Services is a critical framework for building secure, compliant, and efficient applications in a high-stakes industry. By integrating security into the SDLC, financial institutions can mitigate risks, meet regulatory requirements, and maintain customer trust. Future trends include increased adoption of AI-driven security tools and GitOps for enhanced automation (,). To get started, explore tools like Snyk, OWASP ZAP, and Terraform, and foster a culture of collaboration and security.