1. Introduction & Overview
What is Automation?
Automation in DevSecOps refers to the use of tools, scripts, and processes to streamline and secure the software development lifecycle, integrating development, security, and operations seamlessly. It minimizes manual intervention, reduces errors, and enhances efficiency in delivering secure software.
History or Background
Historically, software development was siloed, with development, security, and operations teams working independently, leading to delays and vulnerabilities. The rise of DevOps in the early 2010s emphasized automation for faster delivery through continuous integration and continuous deployment (CI/CD). DevSecOps evolved by embedding security into this pipeline, making automation critical for scaling security practices without sacrificing speed.
Why is it Relevant in DevSecOps?
Automation is pivotal in DevSecOps for:
- Speed and Scale: Automates repetitive tasks like code testing, security scanning, and deployment, enabling rapid delivery.
- Security Integration: Embeds security checks (e.g., static analysis, vulnerability scanning) into CI/CD pipelines.
- Consistency: Ensures standardized processes, reducing human error and ensuring compliance with security policies.
- Collaboration: Bridges gaps between development, security, and operations teams through shared automated workflows.
2. Core Concepts & Terminology
Key Terms and Definitions
- CI/CD Pipeline: A series of automated steps for building, testing, and deploying code.
- Infrastructure as Code (IaC): Managing infrastructure through machine-readable scripts (e.g., Terraform, Ansible).
- Static Application Security Testing (SAST): Automated scanning of source code for vulnerabilities.
- Dynamic Application Security Testing (DAST): Testing running applications for security issues.
- Continuous Monitoring: Automated tracking of application and infrastructure health post-deployment.
| Term | Definition |
|---|---|
| CI/CD | Continuous Integration and Continuous Delivery/Deployment. Automated pipelines for code building, testing, and deploying. |
| Infrastructure as Code (IaC) | Managing and provisioning infrastructure through machine-readable scripts. |
| Security as Code (SaC) | Embedding security policies and checks in code and pipelines. |
| Policy as Code (PaC) | Defining security and compliance rules in code (e.g., Open Policy Agent). |
| Automation Pipeline | A sequence of tasks automated within the SDLC, including testing, scanning, and deployment. |
How it Fits into the DevSecOps Lifecycle
Automation integrates into the DevSecOps lifecycle at:
- Plan: Automating requirement analysis with tools like Jira.
- Code: Linting and SAST for early vulnerability detection.
- Build: Automated compilation and dependency management.
- Test: Unit, integration, and security tests (e.g., OWASP ZAP).
- Deploy: Automated deployments via tools like Jenkins or GitLab CI.
- Operate/Monitor: Real-time monitoring with tools like Prometheus.
3. Architecture & How It Works
Components and Internal Workflow
Automation in DevSecOps relies on a modular architecture:
- Version Control: Stores code and configurations (e.g., Git).
- CI/CD Tools: Orchestrate pipelines (e.g., Jenkins, GitLab CI).
- Security Tools: Perform SAST/DAST (e.g., Snyk, SonarQube).
- Infrastructure Tools: Manage environments (e.g., Terraform, Kubernetes).
- Monitoring Tools: Track performance and security (e.g., Prometheus, Splunk).
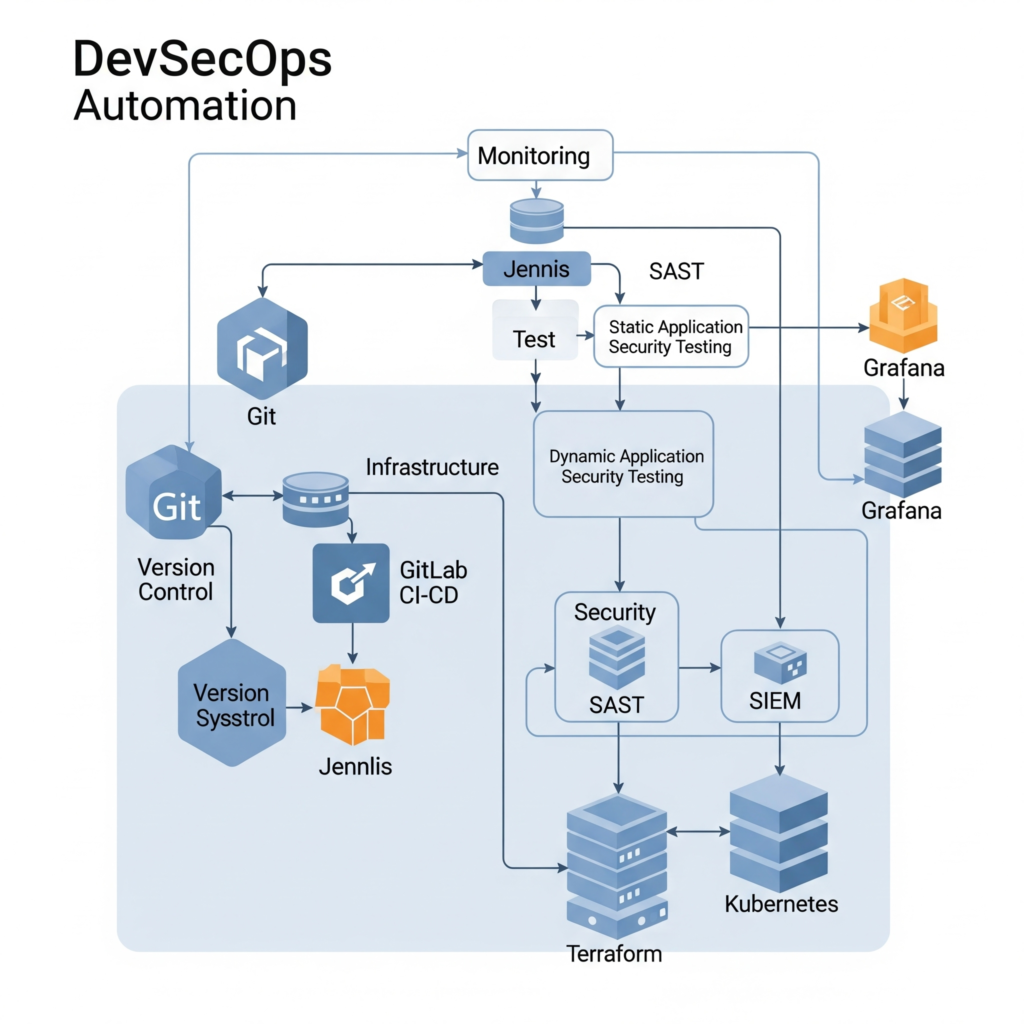
The workflow starts with code commits triggering automated builds, tests, and security scans, followed by deployment to production or staging environments, with continuous monitoring for anomalies.
# Example GitHub Action for automated SAST + SCA
name: Security Checks
on: [push]
jobs:
security:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v3
- name: Run Trivy SCA
run: trivy fs .
- name: Run Semgrep SAST
run: semgrep scan --config=auto
Architecture Diagram
The architecture can be visualized as a pipeline:
- Input: Code commits to a Git repository.
- Stages: Build -> Test (unit, integration, SAST, DAST) -> Deploy (IaC, container orchestration) -> Monitor.
- Feedback Loop: Monitoring data feeds back to developers for improvements.
+---------------------+ +-----------------------+ +---------------------+
| Developer Pushes | ---> | CI/CD Pipeline | ---> | Security Scans |
| Code to Repo | | (e.g., Jenkins, GH) | | (SAST, SCA, IaC) |
+---------------------+ +-----------------------+ +---------------------+
|
v
+-----------------------------+
| Deployment + Infra Checks |
+-----------------------------+
|
v
+-----------------------------+
| Runtime Monitoring + Alerts|
+-----------------------------+
Integration Points with CI/CD or Cloud Tools
Automation integrates with:
- CI/CD Tools: Jenkins scripts for pipeline orchestration, GitLab CI for native integration.
- Cloud Platforms: AWS CodePipeline, Azure DevOps for cloud-native automation.
- Containerization: Docker and Kubernetes for automated deployments.
4. Installation & Getting Started
Basic Setup or Prerequisites
To set up a basic DevSecOps automation pipeline, you need:
- A Git repository (e.g., GitHub, GitLab).
- Jenkins or GitLab CI installed.
- Security tools like Snyk or OWASP ZAP.
- A cloud provider (e.g., AWS, Azure) or local server.
- Basic knowledge of YAML and shell scripting.
Hands-on: Step-by-Step Beginner-Friendly Setup Guide
Here’s a guide to set up a Jenkins-based DevSecOps pipeline:
- Install Jenkins:
sudo apt update
sudo apt install openjdk-11-jdk -y
wget -q -O - https://pkg.jenkins.io/debian/jenkins.io.key | sudo apt-key add -
sudo sh -c 'echo deb http://pkg.jenkins.io/debian-stable binary/ > /etc/apt/sources.list.d/jenkins.list'
sudo apt update
sudo apt install jenkins -yAccess Jenkins at http://localhost:8080 and complete the setup wizard.
- Configure Git Repository: Create a GitHub repository and push a sample application.
- Set Up Pipeline:
- In Jenkins, create a new pipeline project.
- Use the following
Jenkinsfilefor automation:
pipeline {
agent any
stages {
stage('Build') {
steps {
sh 'echo Building...'
// Add build commands (e.g., mvn clean install)
}
}
stage('Security Scan') {
steps {
sh 'snyk test' // Assumes Snyk CLI installed
}
}
stage('Deploy') {
steps {
sh 'echo Deploying to staging...'
// Add deployment commands
}
}
}
}4. Install Snyk: Follow Snyk’s documentation to install the CLI and integrate it with Jenkins.
5. Test the Pipeline: Commit changes to the Git repository to trigger the pipeline.
5. Real-World Use Cases
DevSecOps Scenarios
Automation shines in these scenarios:
- Automated Vulnerability Scanning: A fintech company uses Snyk in its CI/CD pipeline to scan Node.js dependencies for vulnerabilities before deployment, reducing security risks.
- Infrastructure Compliance: A healthcare provider uses Terraform to automate AWS infrastructure setup, ensuring HIPAA-compliant configurations.
- Container Security: An e-commerce platform integrates Trivy to scan Docker images for vulnerabilities in its Kubernetes-based pipeline.
- Incident Response: A SaaS company uses automated alerts from Prometheus to detect and mitigate unauthorized access attempts in real time.
Industry-Specific Examples
- Finance: Automating PCI-DSS compliance checks in CI/CD pipelines.
- Healthcare: Ensuring HIPAA compliance through automated IaC scans.
6. Benefits & Limitations
Key Advantages
- Efficiency: Reduces manual effort, speeding up delivery.
- Security: Embeds security checks early and often.
- Scalability: Handles large-scale deployments with consistency.
- Traceability: Provides audit trails for compliance.
Common Challenges or Limitations
- Complexity: Setting up and maintaining pipelines can be complex.
- Tool Overload: Too many tools can lead to integration challenges.
- False Positives: Security scans may generate noise, requiring manual review.
- Cost: Cloud-based automation tools can be expensive.
7. Best Practices & Recommendations
Security Tips, Performance, Maintenance
- Shift Left: Integrate security tools early in the pipeline.
- Least Privilege: Use minimal permissions for automation scripts.
- Regular Updates: Keep tools and dependencies updated to avoid vulnerabilities.
- Monitoring: Set up alerts for pipeline failures or security issues.
Compliance Alignment, Automation Ideas
- Use tools like HashiCorp Sentinel for policy-as-code to enforce compliance.
- Automate audit logging for GDPR, HIPAA, or SOC 2 compliance.
8. Comparison with Alternatives
Comparison Table
| Feature | Jenkins | GitLab CI | AWS CodePipeline |
|-----------------------|-----------------|-----------------|------------------|
| Open Source | Yes | Yes | No |
| Cloud-Native | No | Yes | Yes |
| Security Integration | Plugins (e.g., Snyk) | Built-in SAST | AWS-native tools |
| Ease of Setup | Moderate | Easy | Easy |
| Cost | Free | Free/Paid | Paid |When to Choose Automation
- Choose Jenkins for flexibility and open-source needs.
- Choose GitLab CI for integrated DevSecOps features.
- Choose AWS CodePipeline for seamless AWS integration.
9. Conclusion
Final Thoughts
Automation is the backbone of DevSecOps, enabling secure, fast, and scalable software delivery. By embedding security into automated CI/CD pipelines, teams can achieve compliance and efficiency simultaneously.
Future Trends
Future trends include AI-driven automation for predictive security analytics and increased adoption of policy-as-code for compliance.