1. Introduction & Overview
What is Operational Expenditure (OpEx)?
Operational Expenditure (OpEx) refers to the ongoing, recurring costs associated with maintaining and operating an organization’s IT infrastructure, applications, and services. In DevSecOps, OpEx includes expenses for cloud services, software licenses, security monitoring, personnel, and other resources needed to sustain development, security, and operations workflows. Unlike one-time investments, OpEx is usage-based and aligns with the pay-as-you-go model common in cloud environments.
History or Background
The concept of OpEx gained prominence in the early 2000s with the advent of cloud computing and the shift toward DevSecOps practices. Traditional IT relied heavily on Capital Expenditure (CapEx) for purchasing physical servers and data centers. However, cloud providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) introduced flexible, subscription-based models, making OpEx central to modern IT operations. This shift enabled organizations to adopt agile, scalable, and secure development practices, which are core to DevSecOps.
Why is it Relevant in DevSecOps?
OpEx is critical in DevSecOps for several reasons:
- Scalability: Cloud-based DevSecOps tools scale dynamically, with costs tied to usage.
- Security: Continuous monitoring and automated security tools contribute to recurring operational costs.
- Agility: OpEx supports rapid iteration and deployment, aligning with DevSecOps’ focus on speed and collaboration.
- Compliance: Regular audits and compliance checks, essential for security, are part of OpEx.
2. Core Concepts & Terminology
Key Terms and Definitions
- OpEx: Recurring costs for running IT operations, such as cloud subscriptions, licenses, and support.
- CapEx: Upfront capital investments, such as purchasing servers or data centers.
- DevSecOps: A methodology integrating development, security, and operations for continuous delivery with security embedded throughout.
- Cost Optimization: Strategies to minimize OpEx while maintaining performance and security.
- Cloud-Native: Applications designed for cloud environments, heavily reliant on OpEx models.
How It Fits into the DevSecOps Lifecycle
OpEx is embedded across the DevSecOps lifecycle, influencing each phase:
- Plan: Budgeting for tools like Jira, Confluence, or GitLab for project management.
- Code: Costs for integrated development environments (IDEs), code repositories, and version control systems (e.g., GitHub).
- Build: Continuous Integration/Continuous Deployment (CI/CD) tools like Jenkins or GitHub Actions incur usage-based costs.
- Test: Automated testing platforms and security scanning tools, such as Snyk or OWASP ZAP.
- Deploy: Cloud infrastructure costs for Kubernetes clusters or serverless deployments (e.g., AWS Lambda).
- Operate: Monitoring tools like Datadog or Splunk for performance and incident response.
- Monitor: Continuous security and performance monitoring to ensure system reliability.
3. Architecture & How It Works
Components and Internal Workflow
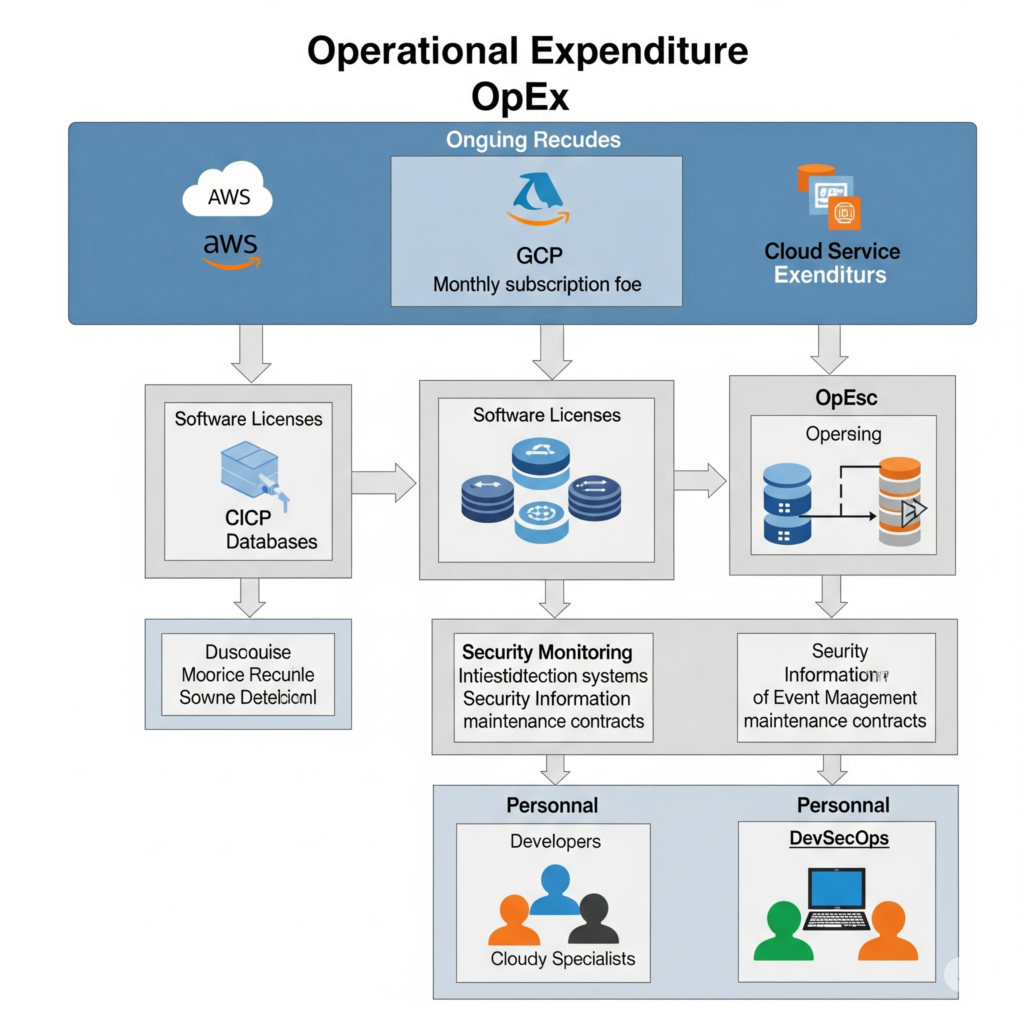
OpEx in DevSecOps comprises several components:
- Cloud Services: Compute (e.g., AWS EC2), storage (e.g., S3), and networking resources.
- Tools and Platforms: CI/CD pipelines, monitoring, and security tools.
- Personnel: DevOps engineers, security analysts, and support staff salaries.
- Licensing: Subscriptions for proprietary software or Software-as-a-Service (SaaS) platforms.
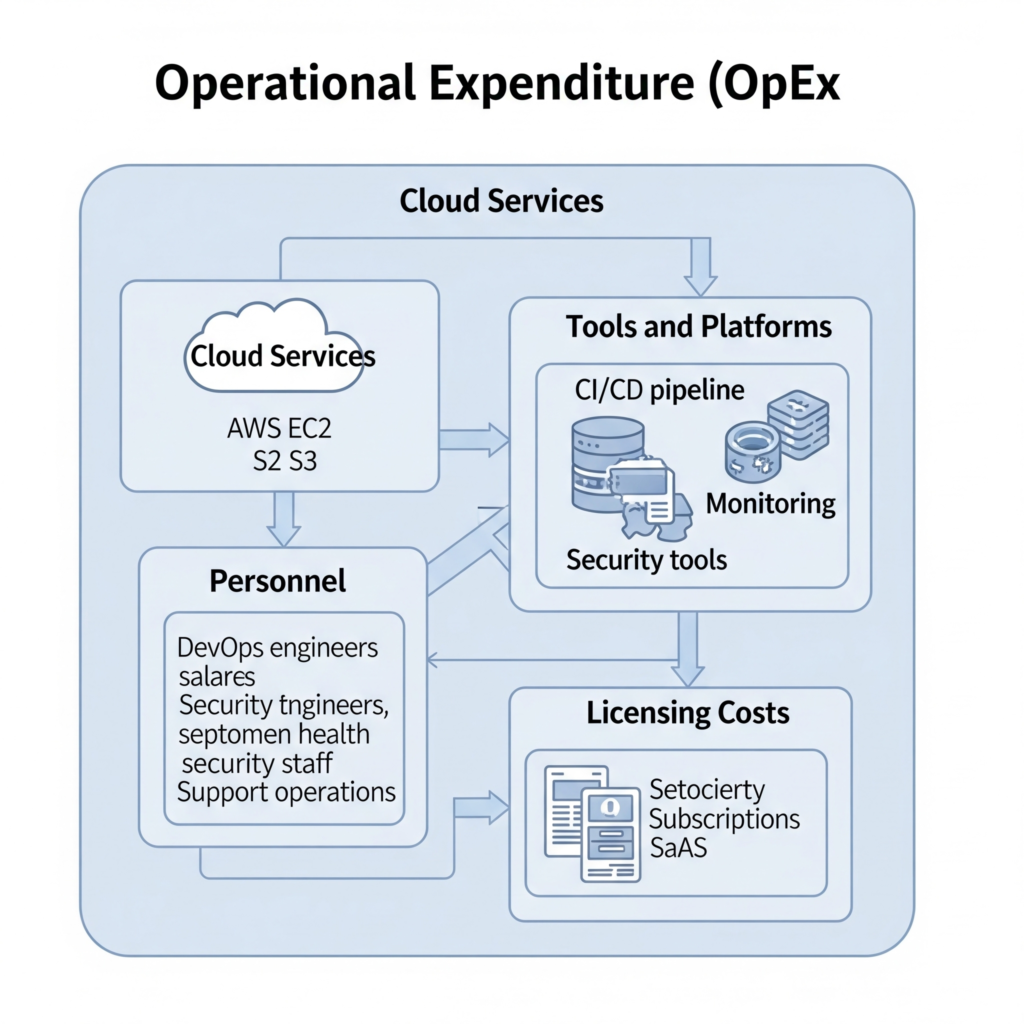
The workflow begins with provisioning cloud resources, followed by integrating them into CI/CD pipelines for building, testing, and deploying applications. Security and monitoring tools run continuously, generating usage-based costs tracked through cloud cost management tools.
Architecture Diagram
Imagine a conceptual architecture diagram with:
- A cloud provider (e.g., AWS) at the core, hosting compute and storage resources.
- CI/CD pipelines (e.g., Jenkins, GitLab) feeding into Kubernetes clusters or serverless functions.
- Security tools (e.g., Snyk, Splunk) integrated at each pipeline stage for vulnerability scanning and monitoring.
- Monitoring dashboards (e.g., Grafana, AWS CloudWatch) tracking costs, performance, and security metrics in real-time.
Integration Points with CI/CD or Cloud Tools
OpEx integrates with DevSecOps tools at multiple points:
- CI/CD: Tools like Jenkins, CircleCI, or GitLab CI/CD incur costs based on build minutes or pipeline usage.
- Cloud Tools: AWS Cost Explorer, Azure Cost Management, or GCP Billing track OpEx in real-time.
- Security: Tools like Qualys, CrowdStrike, or Snyk provide vulnerability scanning and threat detection, contributing to OpEx.
4. Installation & Getting Started
Basic Setup or Prerequisites
To manage OpEx in a DevSecOps environment, you need:
- A cloud account with a provider like AWS, Azure, or GCP.
- Access to a CI/CD tool (e.g., Jenkins, GitLab, or GitHub Actions).
- Monitoring tools (e.g., Prometheus, Grafana, or Datadog).
- Basic knowledge of cloud cost management and budgeting.
Hands-on: Step-by-Step Beginner-Friendly Setup Guide
Follow these steps to set up a basic DevSecOps environment with OpEx tracking:
- Set Up an AWS Account:
- Sign up at https://aws.amazon.com.
- Enable AWS Cost Explorer in the AWS Management Console to track costs.
- Set up a billing alert to monitor usage.
- Configure a CI/CD Pipeline:
- Install Jenkins on an AWS EC2 instance:
sudo apt update sudo apt install openjdk-11-jdk -y wget -q -O - https://pkg.jenkins.io/debian/jenkins.io.key | sudo apt-key add - sudo sh -c 'echo deb http://pkg.jenkins.io/debian-stable binary/ > /etc/apt/sources.list.d/jenkins.list' sudo apt update sudo apt install jenkins -y - Access Jenkins at
http://<ec2-public-ip>:8080and configure a basic pipeline.
- Integrate Security Tools:
- Install Snyk for vulnerability scanning:
npm install -g snyk snyk auth - Run
snyk testin your project directory to scan for vulnerabilities.
- Set Up Monitoring:
- Deploy Prometheus and Grafana using Docker:
docker run -d -p 9090:9090 prom/prometheus docker run -d -p 3000:3000 grafana/grafana - Access Grafana at
http://<ec2-public-ip>:3000and configure dashboards to monitor system metrics.
- Track OpEx:
- Use AWS Cost Explorer to set budgets and monitor usage.
- Create cost allocation tags (e.g., by project or team) for granular tracking.
5. Real-World Use Cases
Here are four real-world scenarios where OpEx is applied in DevSecOps:
- E-commerce Platform:
An online retailer uses AWS Lambda for serverless microservices and Snyk for security scanning. OpEx covers compute costs for Lambda and subscription fees for Snyk, ensuring secure and scalable deployments. - Financial Services:
A bank leverages Azure DevOps for CI/CD and Qualys for compliance scanning. OpEx includes pipeline usage costs and regular audits to meet regulatory standards like PCI-DSS. - Healthcare:
A telemedicine application runs on GCP Kubernetes clusters with Splunk for log analysis. OpEx covers cluster management and monitoring costs, ensuring HIPAA compliance and system reliability. - Gaming Industry:
A game studio uses GitLab CI/CD for rapid deployments and Datadog for performance monitoring. OpEx includes build minute costs and real-time analytics to optimize user experience.
6. Benefits & Limitations
Key Advantages
- Flexibility: The pay-as-you-go model supports dynamic scaling without upfront investments.
- Predictability: Tools like AWS Cost Explorer provide real-time cost visibility.
- Agility: OpEx enables rapid deployment and iteration, aligning with DevSecOps principles.
- Security: Funds continuous monitoring and compliance checks for robust security.
Common Challenges or Limitations
- Cost Overruns: Unmonitored cloud usage can lead to unexpected expenses.
- Complexity: Managing multiple tools and subscriptions increases operational overhead.
- Vendor Lock-in: Reliance on specific cloud providers may limit flexibility and increase long-term costs.
7. Best Practices & Recommendations
- Cost Optimization: Use reserved instances or spot instances for cost savings in cloud environments.
- Security: Integrate security tools like Snyk or OWASP ZAP early in the CI/CD pipeline to catch vulnerabilities.
- Automation: Automate cost monitoring with tools like AWS Budgets or Azure Cost Management.
- Compliance: Align with standards like GDPR, HIPAA, or PCI-DSS using automated audit tools.
- Tagging: Apply cost allocation tags to resources (e.g., by project, team, or environment) for granular tracking.
- Regular Reviews: Conduct monthly cost reviews to identify and eliminate unused resources.
8. Comparison with Alternatives
| Criteria | OpEx | CapEx |
|---|---|---|
| Cost Model | Recurring, usage-based | Upfront investment |
| Scalability | Highly scalable with cloud | Limited by hardware capacity |
| DevSecOps Fit | Aligns with cloud-native tools | Suited for on-premises setups |
| Maintenance | Managed by cloud providers | In-house responsibility |
When to Choose OpEx
Choose OpEx over CapEx when:
- Rapid scaling is required for dynamic workloads.
- Cloud-native or serverless architectures are used.
- Budget flexibility is preferred over large upfront investments.
9. Conclusion
Operational Expenditure (OpEx) is a cornerstone of DevSecOps, enabling organizations to build, deploy, and secure applications with flexibility and agility. By aligning costs with usage, OpEx supports the dynamic nature of cloud-native environments while ensuring continuous security and compliance. As cloud adoption grows, future trends may include AI-driven cost optimization and enhanced automation for security and monitoring.