1. Introduction & Overview
What is a Cloud Center of Excellence (CCoE)?
A Cloud Center of Excellence (CCoE) is a cross-functional team within an organization tasked with leading, governing, and optimizing cloud adoption and management. It serves as a centralized hub to establish best practices, enforce governance, and foster collaboration across IT, security, development, and business units. In the context of DevSecOps, a CCoE integrates security and operational excellence into the software development lifecycle, ensuring that cloud-based solutions are secure, compliant, and efficient.

History or Background
The CCoE concept emerged in the early 2010s as organizations began large-scale cloud migrations to platforms like AWS, Azure, and Google Cloud. Initially, cloud adoption was fragmented, leading to issues like cloud sprawl, inconsistent practices, and security vulnerabilities. The CCoE model was popularized by cloud providers and consultancies (e.g., AWS, Gartner) to address these challenges by creating a structured approach to cloud governance. Over time, as DevSecOps gained traction—emphasizing security integration in development and operations—CCoEs evolved to incorporate DevSecOps principles, ensuring security is embedded from code to cloud.
Why is it Relevant in DevSecOps?
In DevSecOps, security is a shared responsibility across development, security, and operations teams. A CCoE aligns with this philosophy by:
- Centralizing Governance: Enforcing security policies and compliance standards across cloud environments.
- Accelerating Secure Development: Providing reusable, secure deployment patterns for CI/CD pipelines.
- Fostering Collaboration: Bridging silos between developers, security experts, and operations teams to embed security early.
- Optimizing Costs and Risks: Using FinOps and security best practices to manage cloud costs while minimizing vulnerabilities.
A CCoE ensures that DevSecOps practices are scalable, repeatable, and aligned with business objectives, making it a cornerstone for cloud-native organizations.
2. Core Concepts & Terminology
Key Terms and Definitions
- Cloud Center of Excellence (CCoE): A multidisciplinary team responsible for cloud strategy, governance, and adoption.
- DevSecOps: A methodology integrating development, security, and operations to deliver secure software faster.
- Cloud Governance: Policies and tools to manage cloud resources, ensuring compliance, security, and cost efficiency.
- FinOps: Financial operations practices to optimize cloud spending.
- Landing Zone: A pre-configured, secure cloud environment for deploying workloads.
- Infrastructure as Code (IaC): Managing cloud infrastructure through code (e.g., Terraform, AWS CloudFormation).
- Cloud-Native: Applications designed to leverage cloud scalability, resilience, and services.
| Term | Definition |
|---|---|
| Cloud Governance | Policies and procedures to manage cloud usage. |
| Guardrails | Predefined rules (IAM roles, security groups) to enforce governance. |
| Landing Zone | Preconfigured cloud environment adhering to best practices. |
| Policy-as-Code | Managing policies in version-controlled code to ensure compliance. |
| FinOps | Cloud financial management to optimize cost. |
| DevSecOps | Practice of integrating security throughout the DevOps lifecycle. |
How it Fits into the DevSecOps Lifecycle
The DevSecOps lifecycle includes planning, coding, building, testing, releasing, deploying, operating, and monitoring. A CCoE supports this lifecycle by:
- Planning: Defining cloud adoption strategies and security requirements.
- Coding/Building: Providing secure IaC templates and CI/CD pipeline configurations.
- Testing: Enforcing automated security scans (e.g., static code analysis, vulnerability scanning).
- Releasing/Deploying: Standardizing deployment processes with governance guardrails.
- Operating/Monitoring: Implementing monitoring tools and incident response plans for cloud environments.
The CCoE acts as an enabler, ensuring that security is integrated at every stage while maintaining agility and operational efficiency.
3. Architecture & How It Works
Components
A CCoE typically includes:
- Leadership: Executive sponsors (e.g., CTO, CISO) for strategic alignment.
- Cloud Architects: Design secure, scalable cloud solutions.
- Security Experts: Ensure compliance and implement security controls.
- DevOps Engineers: Automate CI/CD pipelines and IaC.
- FinOps Specialists: Optimize cloud costs.
- Business Analysts: Align cloud initiatives with business goals.
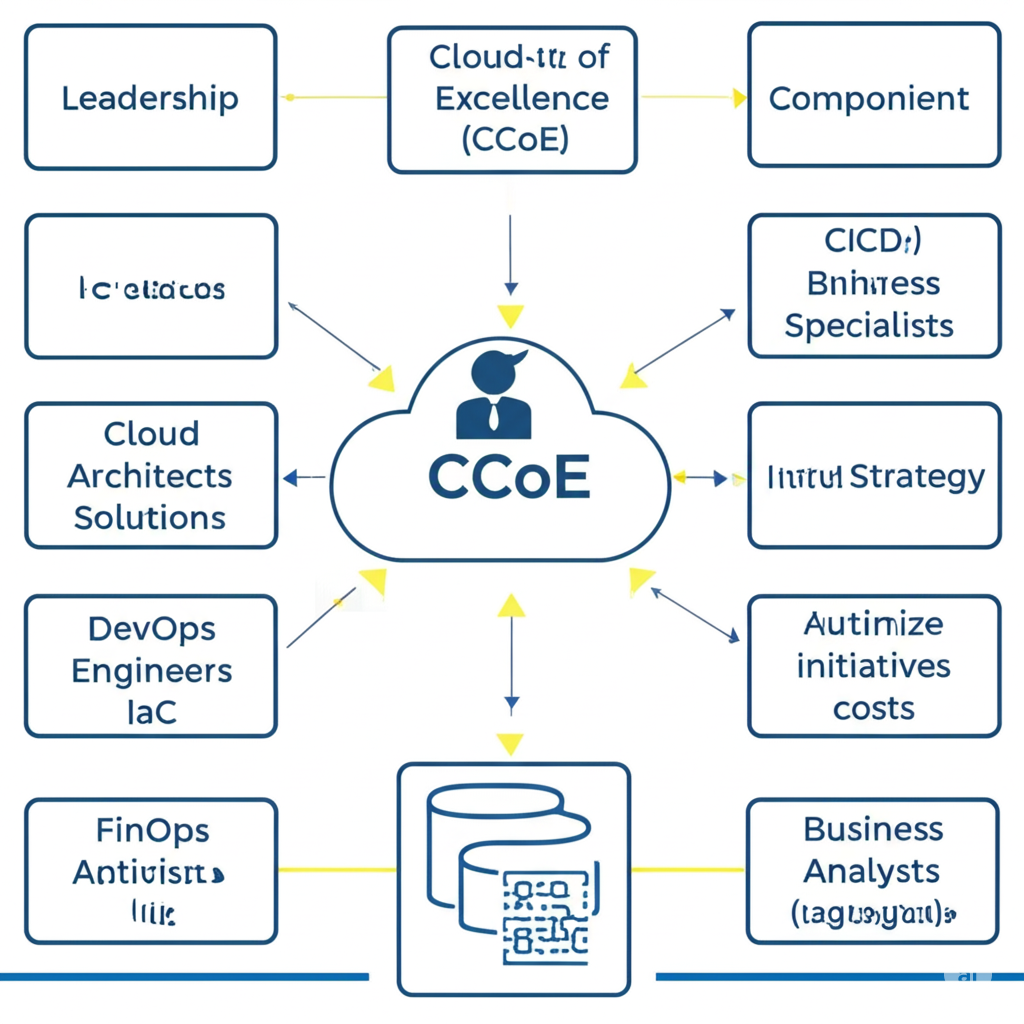
Internal Workflow
The CCoE operates as a hub-and-spoke model:
- Strategy Definition: Leadership defines cloud and DevSecOps goals.
- Policy Creation: Security and governance teams establish policies (e.g., encryption, access control).
- Tooling and Automation: DevOps engineers develop reusable templates and pipelines.
- Knowledge Sharing: Community efforts (e.g., training, wikis) disseminate best practices.
- Monitoring and Optimization: Continuous assessment of cloud usage, costs, and security posture.
Architecture Diagram Description
Imagine a hub-and-spoke diagram:
- Hub (CCoE): A central team with roles like Cloud Architect, Security Specialist, and FinOps Analyst.
- Spokes: Business units, development teams, and operations teams interacting with the CCoE.
- Connections: Represented by workflows like policy enforcement, training sessions, and automated pipelines.
- Cloud Environment: A landing zone with services like AWS EC2, Azure AKS, or Google Cloud Storage, integrated with CI/CD tools (e.g., Jenkins, GitLab).
Dev Teams -> CI/CD -> Cloud APIs
↑
Policies from CCoE
↑
Security Tools ← CCoE Governance ← Monitoring
Integration Points with CI/CD or Cloud Tools
- CI/CD Pipelines: The CCoE integrates tools like Jenkins, GitLab CI, or AWS CodePipeline with security scanning (e.g., Snyk, Checkmarx) and IaC validation.
- Cloud-Native Tools: Uses AWS Config, Azure Policy, or Google Cloud Security Command Center for governance.
- Monitoring: Integrates with tools like Prometheus, Datadog, or AWS CloudWatch for real-time security and performance monitoring.
Example IaC Snippet (Terraform for AWS):
resource "aws_s3_bucket" "secure_bucket" {
bucket = "ccoe-secure-bucket"
acl = "private"
versioning {
enabled = true
}
server_side_encryption_configuration {
rule {
apply_server_side_encryption_by_default {
sse_algorithm = "AES256"
}
}
}
}
4. Installation & Getting Started
Basic Setup or Prerequisites
- Team Formation: Assemble a cross-functional team (10–15 members) with roles like cloud architects, security experts, and DevOps engineers.
- Cloud Provider Account: Set up an account (e.g., AWS, Azure, Google Cloud) with administrative access.
- Tools: Install Git, Terraform, and a CI/CD tool (e.g., Jenkins, GitLab).
- Skills: Ensure team members have cloud certifications (e.g., AWS Certified Solutions Architect, Azure Security Engineer).
Hands-On: Step-by-Step Beginner-Friendly Setup Guide
- Define CCoE Objectives:
- Establish goals (e.g., secure cloud migration, cost optimization).
- Create a charter outlining roles and responsibilities.
- Set Up a Cloud Landing Zone:
- Use a cloud provider’s landing zone solution (e.g., AWS Control Tower, Azure Landing Zone).
- Example AWS CLI command to initialize Control Tower:
aws controltower create-landing-zone --manifest-file landing-zone-config.json3. Configure Governance Policies:
- Define policies for IAM, encryption, and tagging.
- Example AWS IAM policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": ["s3:ListBucket"],
"Resource": ["arn:aws:s3:::ccoe-secure-bucket"]
}
]
}4. Integrate CI/CD Pipeline:
- Set up a Git repository and CI/CD tool.
- Example GitLab CI configuration:
stages:
- test
- deploy
security_scan:
stage: test
script:
- snyk test
deploy_to_aws:
stage: deploy
script:
- terraform apply -auto-approve5. Train Teams:
- Host workshops on cloud security and DevSecOps practices.
- Use platforms like LinkedIn Learning or cloud provider training.
5. Real-World Use Cases
Scenario 1: Secure Application Deployment
A financial services company uses a CCoE to deploy a customer-facing application on AWS. The CCoE:
- Implements secure IaC templates with encryption and IAM roles.
- Integrates Snyk for vulnerability scanning in the CI/CD pipeline.
- Ensures PCI-DSS compliance through automated audits.
Scenario 2: Multi-Cloud Cost Optimization
A retail organization with a hybrid AWS/Azure setup leverages the CCoE to:
- Use FinOps tools (e.g., CloudHealth) to monitor spending.
- Automate resource tagging to track costs by department.
- Reduce costs by 20% through right-sizing instances.
Scenario 3: Incident Response Automation
A healthcare provider uses the CCoE to enhance incident response:
- Configures AWS CloudTrail and Security Hub for monitoring.
- Automates remediation using AWS Systems Manager runbooks.
- Achieves HIPAA compliance with encrypted data storage.
Scenario 4: Developer Self-Service
A tech startup empowers developers with a CCoE-managed landing zone:
- Provides pre-approved IaC templates for Kubernetes clusters.
- Integrates GitLab CI with security tools like Checkmarx.
- Reduces deployment time by 30% through standardized pipelines.
6. Benefits & Limitations
Key Advantages
- Centralized Governance: Ensures consistent security and compliance across cloud environments.
- Accelerated Innovation: Provides reusable templates, reducing development time.
- Cost Optimization: FinOps practices minimize cloud waste.
- Improved Collaboration: Breaks down silos between development, security, and operations.
Common Challenges or Limitations
- Resistance to Change: Teams may resist centralized governance.
- Skill Gaps: Requires expertise in cloud, DevSecOps, and FinOps.
- Initial Setup Cost: Time and resources needed to establish the CCoE.
- Scalability: May struggle with rapidly growing organizations without proper planning.
7. Best Practices & Recommendations
Security Tips
- Enforce Least Privilege: Use IAM roles with minimal permissions.
- Automate Security Scans: Integrate tools like Snyk or OWASP ZAP in CI/CD pipelines.
- Encrypt Everything: Mandate encryption for data at rest and in transit.
Performance
- Right-Sizing Resources: Use tools like AWS Trusted Advisor to optimize resource usage.
- Monitor Performance: Implement Prometheus or CloudWatch for real-time metrics.
Maintenance
- Regular Policy Reviews: Update governance policies quarterly.
- Continuous Training: Upskill teams on new cloud features and security threats.
Compliance Alignment
- Align with standards like GDPR, HIPAA, or PCI-DSS using automated compliance checks (e.g., AWS Config Rules).
- Example AWS Config Rule:
{
"ConfigRuleName": "s3-bucket-encryption-enabled",
"Source": {
"Owner": "AWS",
"SourceIdentifier": "S3_BUCKET_SERVER_SIDE_ENCRYPTION_ENABLED"
}
}Automation Ideas
- Use AWS CodePipeline or Azure DevOps for automated deployments.
- Implement chatops (e.g., Slack bots) for incident alerts and approvals.
8. Comparison with Alternatives
| Approach | CCoE | Ad-Hoc Cloud Management | External Consultancy |
|---|---|---|---|
| Governance | Centralized, standardized policies | Fragmented, inconsistent | Expert-led but may lack internal context |
| Cost Efficiency | FinOps-driven cost optimization | High risk of overspending | Costly long-term contracts |
| Scalability | Scales with organizational growth | Limited scalability | Scalable but dependent on vendor |
| Security | Embedded DevSecOps practices | Inconsistent security practices | Strong security but may not align with culture |
| When to Choose | Large-scale, long-term cloud adoption with DevSecOps focus | Small, temporary projects | Rapid setup with limited internal expertise |
When to Choose CCoE: Opt for a CCoE when your organization requires sustainable, scalable cloud adoption with integrated DevSecOps practices. It’s ideal for enterprises aiming for long-term cloud maturity.
9. Conclusion
A Cloud Center of Excellence (CCoE) is a transformative framework for organizations adopting cloud technologies within a DevSecOps culture. By centralizing governance, fostering collaboration, and embedding security, a CCoE accelerates cloud adoption while minimizing risks and costs. As cloud technologies evolve, CCoEs will increasingly leverage AI-driven automation and advanced FinOps tools to stay ahead.