1. Introduction & Overview
What is Cloud Financial Management?
Cloud Financial Management (CFM), also known as FinOps or Cloud Cost Management, is the practice of optimizing cloud spending to maximize business value while maintaining operational efficiency. It integrates financial accountability into cloud operations, enabling organizations to monitor, forecast, and optimize costs across dynamic cloud environments. CFM combines tools, processes, and cultural practices to align cloud usage with business objectives, ensuring cost transparency, control, and efficiency.

History or Background
CFM emerged as cloud adoption grew, particularly with the rise of public cloud providers like AWS, Azure, and Google Cloud Platform (GCP) in the early 2010s. Organizations faced challenges with unpredictable cloud costs, leading to the development of FinOps as a discipline. The FinOps Foundation, established in 2019, formalized CFM practices, promoting collaboration between finance, engineering, and operations teams. In DevSecOps, CFM has become critical as organizations integrate security and cost management into rapid development cycles.
Why is it Relevant in DevSecOps?
DevSecOps emphasizes integrating security into every phase of the software development lifecycle (SDLC) while maintaining speed and agility. CFM aligns with DevSecOps by:
- Cost Accountability: Ensures secure cloud resources are cost-effective, preventing overspending on unused or over-provisioned assets.
- Automation: Leverages automated tools to monitor costs in real-time, aligning with DevSecOps’ focus on continuous integration and deployment (CI/CD).
- Compliance: Supports regulatory compliance by tracking resource usage and ensuring cost-effective security measures.
- Cross-Functional Collaboration: Bridges finance, security, development, and operations teams, fostering a shared responsibility model.
2. Core Concepts & Terminology
Key Terms and Definitions
- FinOps: A cultural and operational framework for managing cloud costs, often used interchangeably with CFM.
- Cost Allocation: Assigning cloud costs to specific teams, projects, or business units using tagging or chargeback models.
- Unit Economics: Metrics like cost per CPU hour or cost per GB of RAM to evaluate resource efficiency.
- Right-Sizing: Adjusting cloud resources to match workload requirements, reducing waste.
- Reserved Instances (RIs): Pre-purchased cloud capacity for cost savings over on-demand pricing.
- Savings Plans: Flexible pricing models offered by cloud providers to reduce costs for predictable workloads.
- Showback/Chargeback: Mechanisms to attribute cloud costs to teams for transparency (showback) or direct billing (chargeback).
| Term | Definition |
|---|---|
| FinOps | Practice of cloud financial management. Focuses on collaboration between engineering, finance, and business. |
| Cloud Cost Optimization | Process of reducing unnecessary cloud spend while ensuring performance and security. |
| Showback / Chargeback | Mechanisms for attributing cloud costs to specific teams or business units. |
| Forecasting & Budgeting | Estimating future cloud usage and setting financial limits. |
| Reserved Instances (RIs) / Savings Plans | Commitment-based pricing models to lower costs. |
How CFM Fits into the DevSecOps Lifecycle
CFM integrates into DevSecOps across the SDLC:
- Plan: Define cost budgets and security policies for cloud resources.
- Code: Use Infrastructure as Code (IaC) to provision cost-optimized, secure resources.
- Build: Integrate cost monitoring into CI/CD pipelines to detect overspending early.
- Test: Validate cost efficiency and security compliance during testing phases.
- Deploy: Automate deployment of cost-optimized resources with security controls.
- Monitor: Continuously track costs and security metrics in production, adjusting as needed.
3. Architecture & How It Works
Components
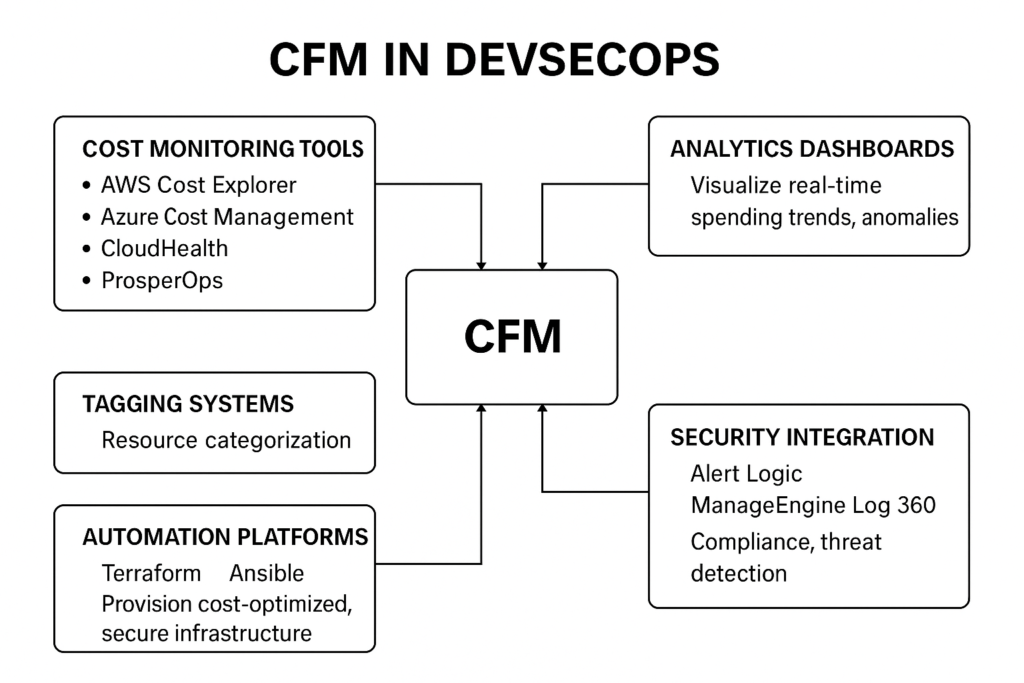
CFM in DevSecOps involves:
- Cost Monitoring Tools: AWS Cost Explorer, Azure Cost Management, or third-party tools like CloudHealth or ProsperOps.
- Tagging Systems: Metadata tags to categorize resources for cost allocation.
- Automation Platforms: Tools like Terraform or Ansible for provisioning cost-optimized, secure infrastructure.
- Analytics Dashboards: Real-time visualizations of spending trends and anomalies.
- Security Integration: Tools like Alert Logic or ManageEngine Log360 for compliance and threat detection.
Internal Workflow
- Data Collection: Cloud providers collect usage data (e.g., compute, storage, network) and associate costs.
- Tagging and Allocation: Resources are tagged (e.g.,
Environment: Production,Team: DevSecOps) for cost tracking. - Analysis: CFM tools analyze usage patterns, identifying inefficiencies or overspending.
- Optimization: Automated actions (e.g., right-sizing instances) or manual adjustments reduce costs.
- Reporting: Dashboards provide insights to stakeholders, aligning costs with business goals.
Architecture Diagram Description
Imagine a layered architecture:
- Top Layer (Dashboards): Displays cost metrics, usage trends, and security alerts.
- Middle Layer (CFM Tools): Processes data from cloud providers, integrating with CI/CD pipelines and security tools.
- Bottom Layer (Cloud Infrastructure): Includes compute (EC2, VMs), storage (S3, Blob), and network resources, tagged for tracking.
- Connections: Bidirectional data flow between layers, with automation scripts (e.g., Terraform) provisioning resources and security tools (e.g., SIEM) monitoring compliance.
+--------------------+
| CI/CD Pipeline | <--- triggers cost-aware deployments
+--------------------+
|
v
+--------------------------+
| Tagging & Provisioning | <--- IaC + Cost tagging
+--------------------------+
|
v
+------------------------------+
| Cloud Provider (AWS, GCP) |
| Billing & Usage APIs |
+------------------------------+
|
v
+------------------------------+
| FinOps Platform (e.g. Apptio)|
| - Cost Analysis |
| - Budgeting & Forecasting |
+------------------------------+
|
v
+------------------------------+
| Reporting & Alerts |
+------------------------------+
Integration Points with CI/CD or Cloud Tools
- CI/CD Pipelines: Embed CFM checks in pipelines using tools like Jenkins or GitLab CI to validate cost policies before deployment.
- IaC Tools: Use Terraform or CloudFormation to define cost-optimized, secure resources.
- Security Tools: Integrate with DevSecOps tools like Snyk or Checkmarx to ensure cost-efficient security configurations.
- Cloud-Native Tools: AWS Budgets, Azure Cost Management, or GCP Cost Management for real-time cost tracking.
4. Installation & Getting Started
Basic Setup or Prerequisites
- Cloud Account: Access to AWS, Azure, or GCP with administrative privileges.
- CFM Tool: Choose a tool like AWS Cost Explorer, Azure Cost Management, or ProsperOps.
- Tagging Strategy: Define a tagging policy (e.g.,
Project,Environment,Owner). - CI/CD Pipeline: A pipeline (e.g., Jenkins, GitLab) for integrating cost checks.
- Basic Knowledge: Familiarity with cloud services, DevSecOps, and IaC.
Hands-On: Step-by-Step Beginner-Friendly Setup Guide
This guide sets up AWS Cost Explorer with a basic tagging strategy integrated into a DevSecOps pipeline.
- Enable AWS Cost Explorer:
- Log in to the AWS Management Console.
- Navigate to Billing and Cost Management > Cost Explorer.
- Enable Cost Explorer (may take 24 hours to activate).
- Define a Tagging Policy:
- Create tags in AWS Tag Editor (e.g.,
Environment: Dev,Team: Security). - Example tagging script using AWS CLI:
- Create tags in AWS Tag Editor (e.g.,
aws resourcegroupstaggingapi tag-resources \
--resource-arn-list arn:aws:ec2:us-east-1:123456789012:instance/i-1234567890abcdef0 \
--tags Environment=Dev,Team=Security3. Set Up Budget Alerts:
- In AWS Budgets, create a budget for a specific project.
- Set thresholds (e.g., $100/month) and email alerts.
- Example AWS CLI command:
aws budgets create-budget \
--account-id 123456789012 \
--budget file://budget.json \
--notifications-with-subscribers file://notifications.json4. Integrate with CI/CD:
- Add a cost validation step in your pipeline (e.g., Jenkins).
- Example Jenkins pipeline snippet:
pipeline {
agent any
stages {
stage('Check Costs') {
steps {
sh 'aws ce get-cost-and-usage --time-period Start=2025-05-01,End=2025-05-31 --granularity MONTHLY --metrics "UnblendedCost"'
}
}
}
}5. Monitor and Optimize:
- Use Cost Explorer to visualize spending.
- Identify idle resources (e.g., unused EC2 instances) and terminate them.
5. Real-World Use Cases
Scenario 1: Fintech Application Deployment
A fintech company uses CFM to manage costs for a microservices-based application. By implementing tagging and AWS Cost Explorer, they allocate costs to development, security, and operations teams. Automated right-sizing scripts reduce EC2 instance sizes, saving 20% on monthly costs while maintaining PCI DSS compliance.
Scenario 2: Multi-Cloud Environment
A retail organization operates on AWS and Azure. Using CloudHealth, they gain unified visibility into spending across both platforms. DevSecOps teams integrate cost checks into CI/CD pipelines, ensuring secure and cost-efficient deployments. This reduces overspending by 15% through optimized resource allocation.
Scenario 3: Compliance-Driven Banking
A bank leverages CFM with ManageEngine Log360 to ensure GDPR compliance. Real-time cost monitoring and automated compliance reports help track secure resource usage, avoiding penalties and reducing costs by 10% through reserved instance purchases.
Scenario 4: Startup Scaling
A startup uses ProsperOps to automate savings plans for AWS workloads. By integrating with their DevSecOps pipeline, they dynamically adjust commitments, achieving a 40% effective savings rate without compromising security or performance.
6. Benefits & Limitations
Key Advantages
- Cost Transparency: Clear visibility into cloud spending by team, project, or resource.
- Automation: Reduces manual effort with AI-driven optimization and real-time alerts.
- Compliance: Aligns with regulatory standards by tracking secure resource usage.
- Collaboration: Fosters alignment between finance, security, and engineering teams.
Common Challenges or Limitations
- Complexity: Managing multi-cloud environments can be challenging without centralized tools.
- Tagging Overhead: Inconsistent tagging can lead to inaccurate cost allocation.
- Learning Curve: Requires understanding of cloud pricing models and DevSecOps integration.
- Tool Costs: Third-party CFM tools may incur additional expenses.
7. Best Practices & Recommendations
- Security Tips:
- Integrate CFM with DevSecOps tools like Alert Logic for real-time threat detection.
- Use IAM roles to restrict access to cost management tools, ensuring security.
- Performance:
- Automate right-sizing with tools like AWS Compute Optimizer.
- Use unit economics (e.g., cost per transaction) to optimize resource allocation.
- Maintenance:
- Regularly review tagging policies to ensure accuracy.
- Schedule monthly cost reviews to identify savings opportunities.
- Compliance Alignment:
- Implement automated compliance checks using tools like ManageEngine Log360.
- Align CFM with standards like GDPR, PCI DSS, or HIPAA.
- Automation Ideas:
- Use Terraform to provision cost-optimized resources:
resource "aws_instance" "example" {
ami = "ami-12345678"
instance_type = "t3.micro" # Cost-optimized instance
tags = {
Environment = "Dev"
Team = "Security"
}
}- Set up anomaly detection alerts in AWS Budgets.
8. Comparison with Alternatives
| Feature | CFM (FinOps) | Traditional Budgeting | Third-Party Tools (e.g., CloudHealth) |
|---|---|---|---|
| Cost Transparency | High, with real-time dashboards | Low, manual tracking | High, unified multi-cloud visibility |
| Automation | Strong, AI-driven optimization | Minimal, spreadsheet-based | Advanced, automated savings plans |
| DevSecOps Integration | Seamless with CI/CD and security | None, siloed approach | Strong, with security integrations |
| Scalability | Scales with cloud usage | Limited, static budgets | Highly scalable across providers |
| Cost | Varies by cloud provider | Free but labor-intensive | Subscription-based, higher cost |
When to Choose CFM
- Choose CFM: For dynamic cloud environments requiring real-time cost tracking, automation, and DevSecOps integration.
- Choose Traditional Budgeting: For small, static environments with minimal cloud usage.
- Choose Third-Party Tools: For multi-cloud setups needing advanced analytics and automation.
9. Conclusion
Cloud Financial Management is a cornerstone of modern DevSecOps, enabling organizations to optimize cloud costs while maintaining security and agility. By integrating CFM into the SDLC, teams can achieve cost transparency, automate optimizations, and align with compliance requirements. As cloud adoption grows, CFM will evolve with AI-driven analytics and deeper DevSecOps integration.