1. Introduction & Overview
What is Optimization in DevSecOps?
Optimization in DevSecOps refers to the practice of enhancing the efficiency, security, and scalability of software development pipelines by embedding security practices into every phase of the DevOps lifecycle. It involves streamlining workflows, automating security checks, and fostering collaboration among development, security, and operations teams to deliver secure software faster and more reliably.
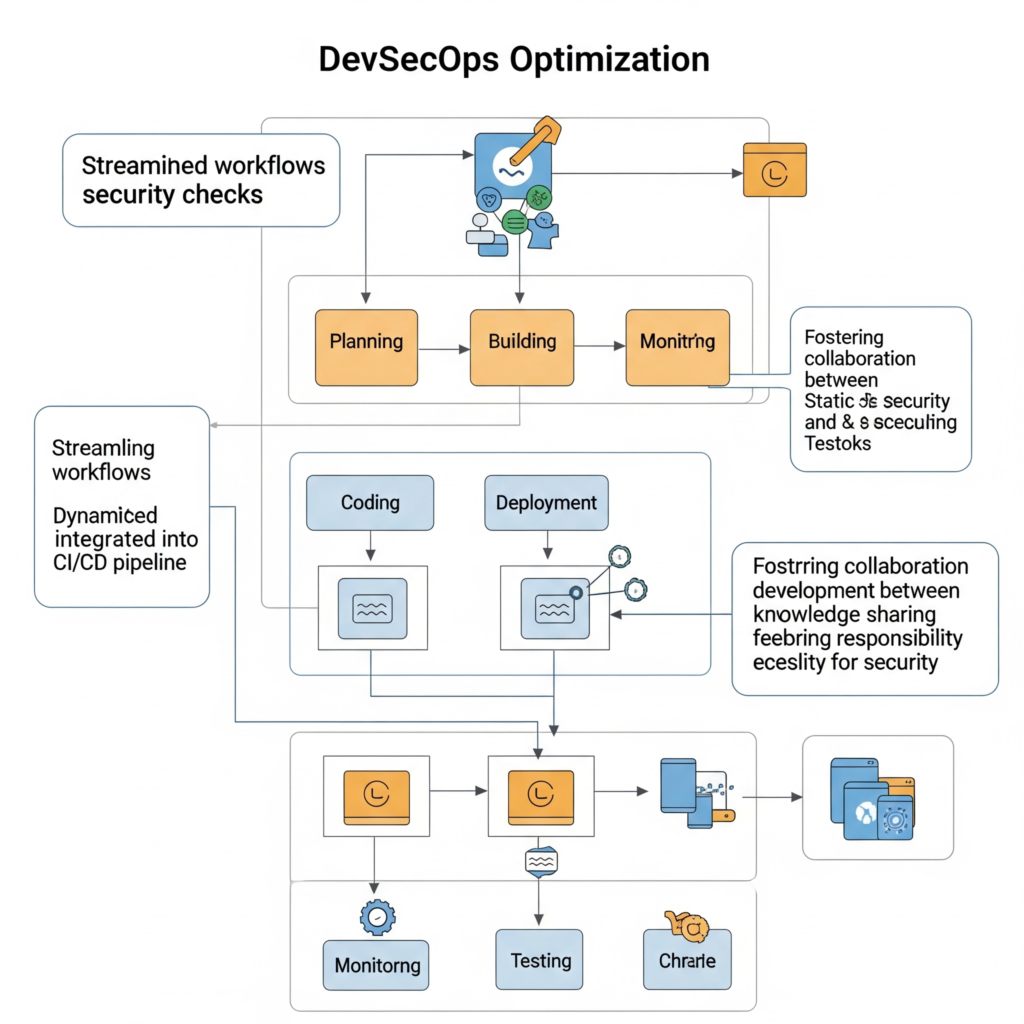
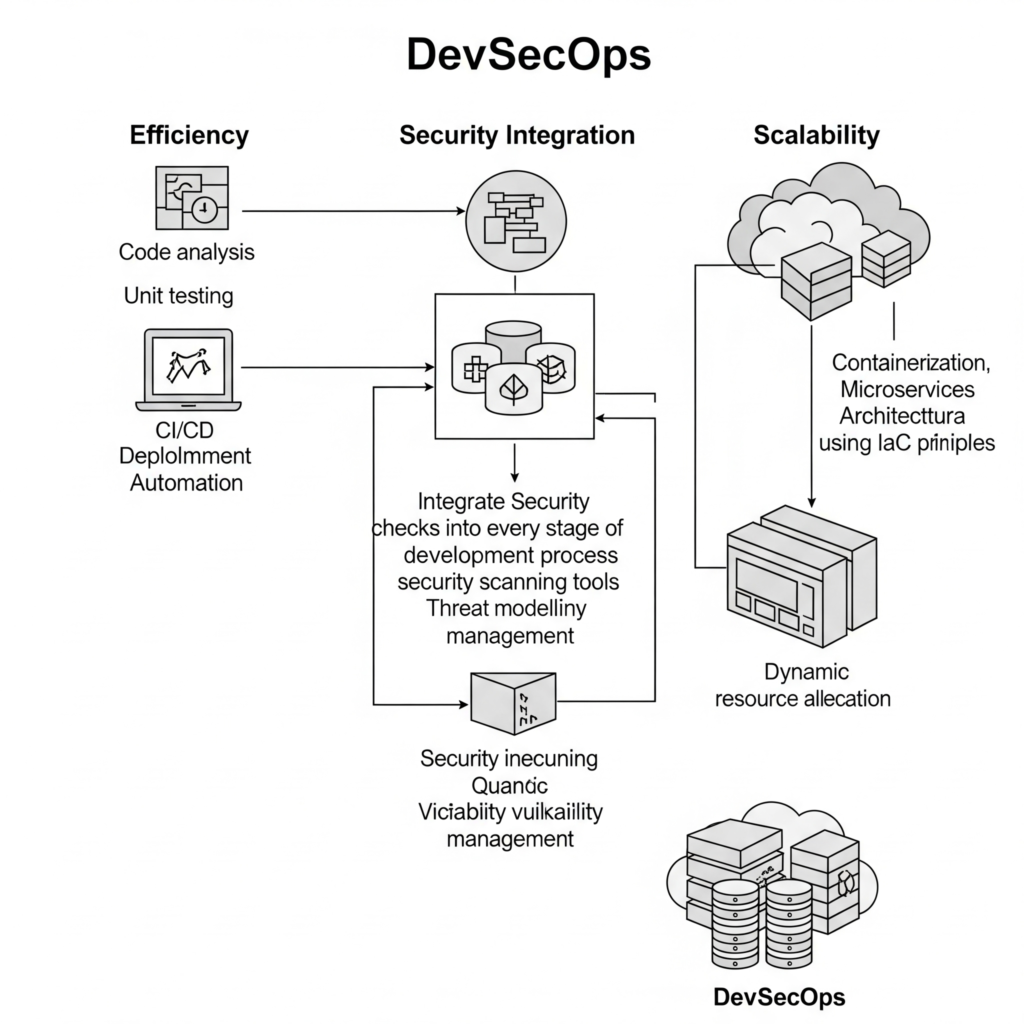
- Key Focus Areas:
- Automating security testing to reduce manual bottlenecks.
- Integrating security tools seamlessly into CI/CD pipelines.
- Improving collaboration to eliminate silos.
- Enhancing visibility and traceability for compliance and auditing.
History or Background
DevSecOps evolved from DevOps, which revolutionized software delivery by combining development and operations for faster release cycles. However, as development speed increased, security was often an afterthought, leading to vulnerabilities in production. DevSecOps emerged around the mid-2010s to address this by integrating security from the start, a concept known as “shift-left security.” Optimization practices within DevSecOps have since grown with advancements in automation tools, cloud-native technologies, and AI-driven security analytics, enabling teams to balance speed, security, and quality.
Why is it Relevant in DevSecOps?
Optimization is critical in DevSecOps because:
- Rising Cyber Threats: With sophisticated attacks targeting software supply chains, optimizing security integration reduces vulnerabilities early.
- Speed and Agility: Faster release cycles demand automated security checks to avoid slowing development.
- Compliance Needs: Regulations like GDPR and HIPAA require continuous security and auditability, which optimization enables.
- Cost Efficiency: Fixing vulnerabilities early in the SDLC is significantly cheaper than post-deployment fixes.
2. Core Concepts & Terminology
Key Terms and Definitions
- Shift-Left Security: Incorporating security practices early in the SDLC, such as during planning and coding.
- CI/CD Pipeline: Continuous Integration/Continuous Deployment pipeline for automating code integration, testing, and deployment.
- SAST (Static Application Security Testing): Analyzes source code for vulnerabilities without executing it.
- DAST (Dynamic Application Security Testing): Tests running applications to identify vulnerabilities like SQL injection.
- IaC (Infrastructure as Code): Managing infrastructure through code for consistent, secure configurations.
- Principle of Least Privilege (PoLP): Granting minimal access to users, processes, or systems to reduce risks.
| Term | Definition |
|---|---|
| Process Instance | An execution of a business workflow in Camunda. |
| Report | A visual representation (e.g., bar chart, heatmap) of process metrics. |
| Dashboard | A customizable panel showing key performance or compliance indicators. |
| Event Log | A chronological record of all activities in a process instance. |
| Flow Node | A task or decision point in a BPMN workflow. |
How It Fits into the DevSecOps Lifecycle
Optimization in DevSecOps integrates security into the following SDLC phases:
- Plan: Define security requirements and threat models.
- Code: Use secure coding practices and static analysis tools.
- Build: Automate security testing in CI pipelines.
- Test: Conduct DAST and penetration testing.
- Deploy: Enforce secure configurations and PoLP.
- Monitor: Continuously monitor for vulnerabilities and anomalies.
This ensures security is a shared responsibility, reducing risks without compromising speed.
3. Architecture & How It Works
Components and Internal Workflow
Optimizing DevSecOps involves several components:
- Security Tools: SAST (e.g., SonarQube), DAST (e.g., OWASP ZAP), and container scanning tools (e.g., Trivy).
- CI/CD Platform: Tools like Jenkins, GitLab CI/CD, or GitHub Actions to automate workflows.
- Monitoring Systems: Tools like Splunk or Wiz for real-time vulnerability detection.
- Collaboration Platforms: Tools like Jira or Slack for cross-team communication.
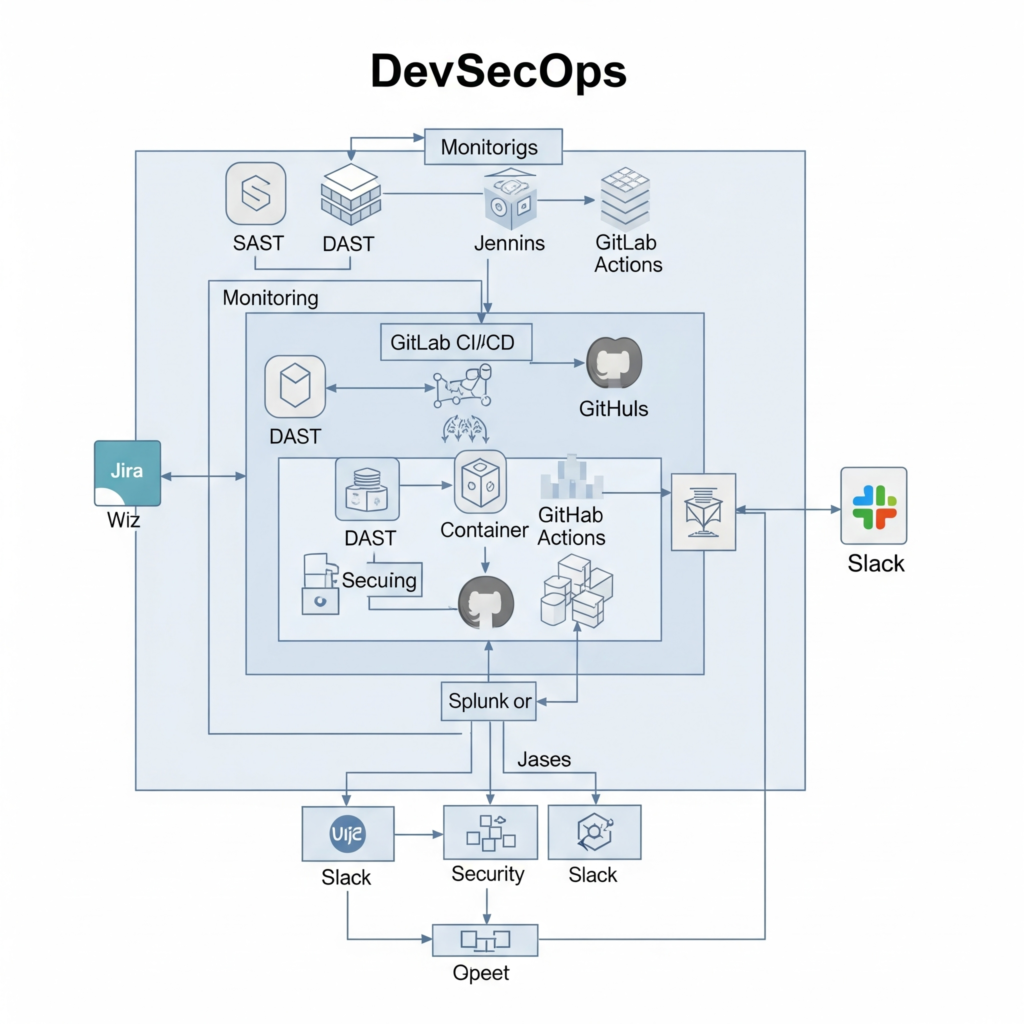
Workflow:
- Plan: Teams define security policies and integrate them into project requirements.
- Code: Developers use IDE plugins (e.g., Checkmarx) for real-time code scanning.
- Build: CI pipelines run automated SAST and dependency checks.
- Test: DAST and penetration tests validate application security.
- Deploy: IaC tools (e.g., Terraform) ensure secure infrastructure.
- Monitor: Continuous monitoring flags runtime issues.
Architecture Diagram Description
Imagine a flowchart with six stages (Plan, Code, Build, Test, Deploy, Monitor). Each stage connects to a central CI/CD pipeline (e.g., Jenkins). Security tools like SonarQube (Code), Trivy (Build), OWASP ZAP (Test), and Wiz (Monitor) integrate at respective stages. Arrows show feedback loops from monitoring to planning, ensuring continuous improvement.
[ Camunda Engine ] ---> [ Elasticsearch ] ---> [ Optimize Server ] ---> [ Web UI ]
^
External Data (optional security logs)
Integration Points with CI/CD or Cloud Tools
- CI/CD Integration: Security tools plug into pipelines via plugins (e.g., Jenkins plugins for Snyk).
- Cloud Tools: AWS Security Hub or Wiz scans cloud configurations for misconfigurations.
- IaC: Terraform or Ansible enforces secure infrastructure settings.
4. Installation & Getting Started
Basic Setup or Prerequisites
To optimize a DevSecOps pipeline, you need:
- A CI/CD tool (e.g., Jenkins, GitLab CI).
- A source code repository (e.g., GitHub, GitLab).
- Security tools (e.g., SonarQube for SAST, Trivy for container scanning).
- A cloud environment (e.g., AWS, Azure) or local servers.
- Basic knowledge of Git, Docker, and YAML for pipeline configuration.
Hands-On: Step-by-Step Setup Guide
Let’s set up a basic DevSecOps pipeline with GitLab CI and Trivy for container scanning.
- Install GitLab Runner:
- On a Linux server, install GitLab Runner:
sudo curl -L --output /usr/local/bin/gitlab-runner https://gitlab-runner-downloads.s3.amazonaws.com/latest/binaries/gitlab-runner-linux-amd64
sudo chmod +x /usr/local/bin/gitlab-runner
gitlab-runner register --url https://gitlab.com/ --registration-token YOUR_TOKEN2. Set Up a GitLab Project:
- Create a new project in GitLab and add a Dockerfile:
FROM node:18
WORKDIR /app
COPY . .
RUN npm install
CMD ["npm", "start"]3. Configure CI/CD Pipeline:
- Create a
.gitlab-ci.ymlfile in your project root:
stages:
- build
- scan
build:
stage: build
script:
- docker build -t my-app:latest .
scan:
stage: scan
image: aquasec/trivy:latest
script:
- trivy image my-app:latest4. Run the Pipeline:
- Push your code to GitLab. The pipeline builds the Docker image and scans it for vulnerabilities.
5. View Results:
- Check the GitLab CI pipeline logs for Trivy’s vulnerability report.
This setup ensures automated container scanning within your CI/CD pipeline.
5. Real-World Use Cases
Scenario 1: E-Commerce Platform Security
An e-commerce company integrates Snyk into its Jenkins pipeline to scan dependencies for vulnerabilities during the build phase. This catches outdated libraries before deployment, preventing exploits like Log4j vulnerabilities.
Scenario 2: Healthcare Compliance
A healthcare provider uses Wiz to scan AWS infrastructure for misconfigurations, ensuring HIPAA compliance. Automated checks in the CI/CD pipeline flag unencrypted S3 buckets, reducing data breach risks.
Scenario 3: Fintech Application Security
A fintech firm employs OWASP ZAP for DAST in its GitHub Actions pipeline. It identifies SQL injection risks in payment APIs during testing, allowing developers to fix issues before production.
Scenario 4: Energy Sector Automation
An energy company uses Terraform for IaC and integrates Trivy to scan container images. This ensures secure deployments of microservices, reducing risks in critical infrastructure.
6. Benefits & Limitations
Key Advantages
- Faster Delivery: Automated security checks reduce manual delays, enabling rapid releases.
- Reduced Vulnerabilities: Early detection lowers the risk of production issues.
- Improved Collaboration: Shared responsibility fosters teamwork across Dev, Sec, and Ops.
- Compliance: Automated audits ensure adherence to regulations like GDPR.
Common Challenges or Limitations
- Cultural Resistance: Teams may resist adopting security practices, slowing adoption.
- Tool Overload: Too many tools can overwhelm developers, leading to inefficiencies.
- False Positives: Automated scans may flag non-issues, requiring manual review.
- Initial Setup Costs: Integrating tools and training teams can be resource-intensive.
7. Best Practices & Recommendations
- Start Small: Begin with one or two security checks (e.g., SAST) to avoid overwhelming teams.
- Automate Everything: Use tools like Snyk or Trivy to automate vulnerability scanning in CI/CD.
- Enforce PoLP: Limit access in production environments to reduce attack surfaces.
- Continuous Training: Train developers on secure coding to reduce vulnerabilities.
- Compliance Alignment: Map tools to standards like NIST 800-53 or OWASP Top 10.
- Monitor Metrics: Track build times, vulnerability counts, and remediation times to measure progress.
8. Comparison with Alternatives
| Feature | Optimized DevSecOps | Traditional Security | Basic DevOps |
|---|---|---|---|
| Security Integration | Early and continuous | End of cycle | Minimal |
| Automation Level | High (SAST, DAST, IaC) | Low (manual audits) | Moderate |
| Speed | Fast | Slow | Fast |
| Collaboration | Cross-functional | Siloed | Dev-Ops only |
| Tool Examples | Snyk, Trivy, Wiz | Nessus, Burp Suite | Jenkins, GitLab |
When to Choose Optimized DevSecOps
- Choose optimized DevSecOps when you need rapid, secure software delivery with compliance requirements.
- Opt for traditional security for legacy systems with infrequent releases.
- Use basic DevOps if security isn’t a primary concern (e.g., internal tools).
9. Conclusion
Optimizing DevSecOps workflows transforms software delivery by embedding security into every SDLC phase, balancing speed and safety. By automating security checks, fostering collaboration, and leveraging tools like Snyk, Trivy, and Wiz, organizations can reduce vulnerabilities and meet compliance needs. Future trends include AI-driven threat detection and zero-trust architectures, which will further enhance DevSecOps efficiency.