1. Introduction & Overview
What is a Procurement Specialist?
A Procurement Specialist is a professional responsible for sourcing, acquiring, and managing goods and services that an organization needs to operate effectively. In the context of DevSecOps, they play a critical role in securing software tools, cloud services, and infrastructure components that support secure, automated, and efficient software development, security, and operations workflows. Their responsibilities include negotiating contracts, ensuring cost-effectiveness, managing supplier relationships, and aligning purchases with organizational security and compliance requirements.

History or Background
Procurement as a discipline has evolved from traditional purchasing to a strategic function that drives organizational efficiency and competitiveness. In the early 2000s, procurement focused on cost reduction and manual processes. With the rise of digital transformation and DevSecOps in the 2010s, procurement specialists began integrating with IT and development teams to source cloud-based tools, automation platforms, and security solutions. Today, they leverage data analytics, AI, and cloud marketplaces to optimize procurement for DevSecOps environments.
Why is it Relevant in DevSecOps?
DevSecOps integrates development, security, and operations to deliver secure software rapidly. Procurement Specialists ensure that the tools and services underpinning DevSecOps—such as CI/CD platforms, security scanners, and cloud infrastructure—are acquired efficiently, comply with regulations, and align with organizational goals. Their role is vital for:
- Cost Optimization: Balancing cost with quality when selecting DevSecOps tools.
- Security and Compliance: Ensuring procured tools meet standards like GDPR, HIPAA, or SOC 2.
- Vendor Management: Negotiating service-level agreements (SLAs) for tools like Jenkins, Snyk, or AWS.
- Scalability: Sourcing scalable cloud solutions to support DevSecOps pipelines.
2. Core Concepts & Terminology
Key Terms and Definitions
- Procurement: The process of acquiring goods and services, including sourcing, negotiating, and purchasing.
- Strategic Sourcing: Identifying and selecting suppliers based on cost, quality, and reliability.
- Supplier Relationship Management (SRM): Building and maintaining partnerships with vendors to ensure consistent service quality.
- CIPS Procurement Cycle: A 13-stage framework for procurement, covering need identification, supplier selection, contract management, and review.
- DevSecOps: A methodology integrating security into DevOps, emphasizing automation, collaboration, and continuous delivery.
- CI/CD: Continuous Integration/Continuous Deployment, automating code integration and deployment.
- Infrastructure as Code (IaC): Managing infrastructure through code, often used in DevSecOps for provisioning cloud resources.
| Term | Definition |
|---|---|
| SaaS Procurement | Acquiring and managing cloud-based software services. |
| Vendor Risk Management | Assessing and mitigating risks associated with third-party tools. |
| SBOM (Software Bill of Materials) | A list of components in a software product, critical for procurement review. |
| Open Source Compliance | Ensuring licenses of open-source software are compliant with internal policies. |
| CAPEX vs OPEX | Capital Expenditure vs Operational Expenditure in procurement decisions. |
How it Fits into the DevSecOps Lifecycle
In DevSecOps, the lifecycle includes planning, coding, building, testing, deploying, operating, and monitoring. Procurement Specialists contribute at multiple stages:
- Planning: Identify tool requirements (e.g., Snyk for vulnerability scanning).
- Building/Testing: Source security tools integrated into CI/CD pipelines.
- Deploying/Operating: Procure cloud services (e.g., AWS EC2, Azure) for deployment.
- Monitoring: Acquire monitoring tools (e.g., Datadog) for observability.
They ensure that tools are cost-effective, secure, and compliant, enabling seamless integration into automated pipelines.
3. Architecture & How It Works
Components and Internal Workflow
The procurement process in DevSecOps involves several components:
- Stakeholders: DevOps engineers, security teams, finance, and procurement specialists.
- Procurement Systems: Tools like SAP Ariba, Coupa, or custom ERP systems for managing purchases.
- DevSecOps Tools: Security scanners (e.g., SonarQube), CI/CD platforms (e.g., Jenkins), and cloud services (e.g., AWS).
- Contracts and SLAs: Agreements defining service expectations, uptime, and security standards.
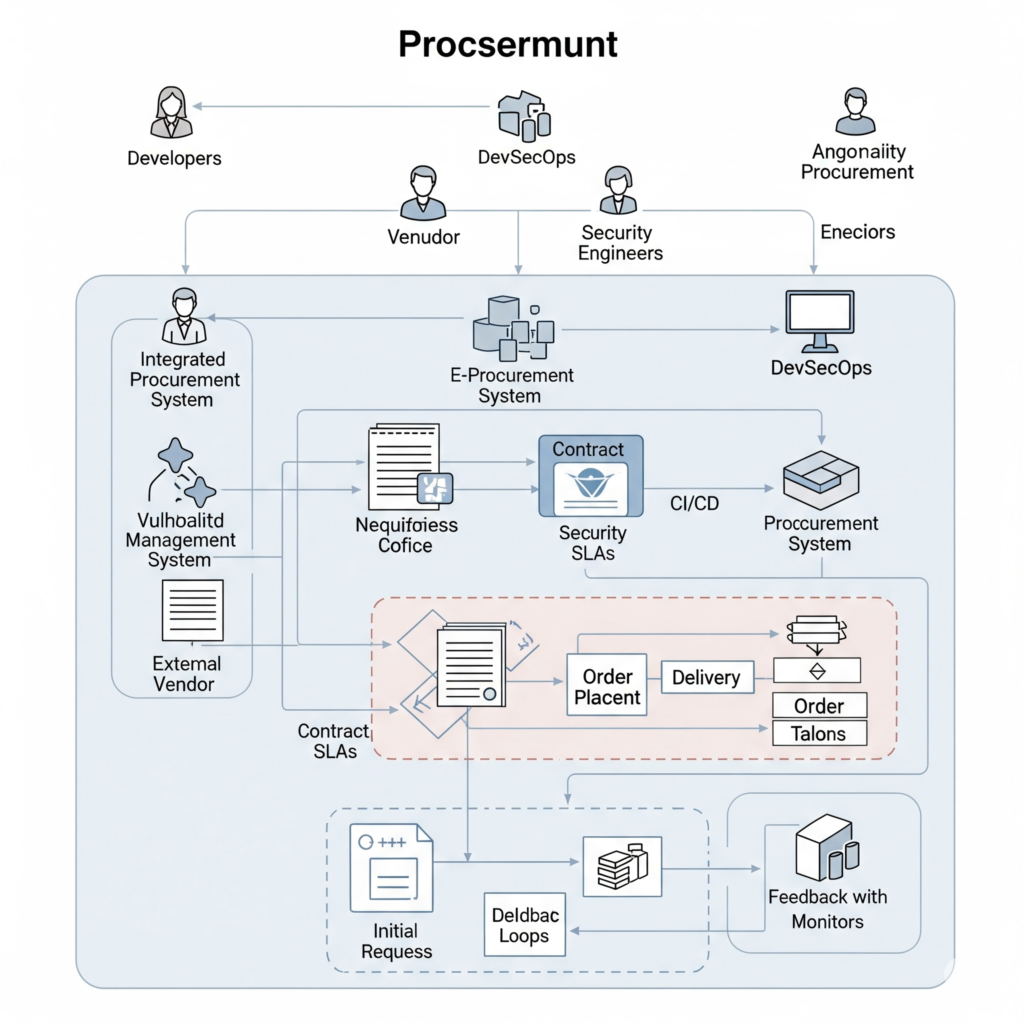
Workflow:
- Need Identification: DevSecOps teams specify tool requirements (e.g., container security).
- Market Research: Procurement Specialists research vendors (e.g., Snyk vs. Aqua Security).
- RFQs/RFPs: Issue Requests for Quotes or Proposals to shortlist vendors.
- Negotiation: Secure favorable terms, focusing on cost, scalability, and compliance.
- Purchase and Integration: Finalize contracts and integrate tools into CI/CD pipelines.
- Monitoring: Track vendor performance and compliance with SLAs.
Architecture Diagram (Text Description)
Imagine a flowchart with three vertical lanes: DevSecOps Team, Procurement Specialist, and Vendors.
- DevSecOps Team Lane: Starts with “Identify Tool Needs” (e.g., SAST tool), flows to “Submit Request” to Procurement.
- Procurement Specialist Lane: Receives request, moves to “Market Research,” “RFQ/RFP Issuance,” “Negotiation,” and “Contract Finalization.”
- Vendors Lane: Responds to RFQs/RFPs, negotiates, and delivers tools/services.
- Integration Point: A horizontal arrow from “Contract Finalization” to “CI/CD Pipeline Integration” in the DevSecOps lane, showing tool deployment.
- Feedback Loop: A dotted line from DevSecOps monitoring back to Procurement for vendor performance reviews.
Integration Points with CI/CD or Cloud Tools
- CI/CD Pipelines: Procurement Specialists source tools like Jenkins or GitLab, integrated via APIs or plugins (e.g., Snyk plugin for Jenkins).
- Cloud Tools: They procure AWS, Azure, or GCP services, often using IaC (e.g., Terraform) for provisioning.
- Security Tools: Tools like OWASP ZAP or SonarQube are integrated into pipelines for automated scans.
Example IaC (Terraform) for AWS Procurement:
provider "aws" {
region = "us-east-1"
}
resource "aws_instance" "devsecops" {
ami = "ami-12345678"
instance_type = "t2.micro"
tags = {
Name = "DevSecOps-Instance"
}
}
4. Installation & Getting Started
Basic Setup or Prerequisites
To act as a Procurement Specialist in DevSecOps, you need:
- Education: Bachelor’s degree in business, supply chain, or related fields.
- Skills: Negotiation, market analysis, familiarity with DevSecOps tools (e.g., Jenkins, Snyk).
- Tools: ERP systems (e.g., SAP), procurement platforms (e.g., Coupa), and basic cloud knowledge.
- Certifications: CIPS Level 4 Diploma, Certified Professional in Supply Management (CPSM).
Hands-On: Step-by-Step Beginner-Friendly Setup Guide
- Learn DevSecOps Basics:
- Take an online course (e.g., Coursera’s “Introduction to DevSecOps”).
- Understand CI/CD, IaC, and security tools.
- Set Up a Procurement Platform:
- Sign up for a free trial of Coupa or SAP Ariba.
- Configure user access for your team.
- Identify a DevSecOps Tool Need:
- Example: Select Snyk for vulnerability scanning.
- Document requirements: open-source support, CI/CD integration, budget ($500/month).
- Research Vendors:
- Use platforms like Gartner or Capterra to compare Snyk, SonarQube, and Checkmarx.
- Shortlist based on cost, features, and reviews.
- Issue an RFQ:
- Draft an RFQ template:
**Request for Quotation: Vulnerability Scanner**
- Budget: $500/month
- Requirements: CI/CD integration, OWASP Top 10 coverage
- Deadline: [Insert Date]Send to vendors via email or procurement platform.
6. Negotiate and Finalize:
- Compare quotes, negotiate discounts, and sign a contract.
- Example: Secure Snyk at $450/month with a 99.9% uptime SLA.
7. Integrate Tool:
- Work with DevSecOps team to add Snyk to Jenkins pipeline
pipeline {
agent any
stages {
stage('Scan') {
steps {
sh 'snyk test'
}
}
}
}5. Real-World Use Cases
Scenario 1: Sourcing CI/CD Tools for a FinTech Company
A FinTech company needs a CI/CD platform to comply with PCI DSS. The Procurement Specialist:
- Researches Jenkins, GitLab, and CircleCI.
- Negotiates a GitLab Enterprise license with enhanced security features.
- Ensures the contract includes audit logs for compliance.
Scenario 2: Procuring Cloud Infrastructure for Scalability
A retail company adopts DevSecOps for e-commerce. The Procurement Specialist:
- Sources AWS EC2 and S3 via AWS Marketplace.
- Uses IaC (Terraform) to provision resources, reducing costs by 15%.
- Negotiates SLAs for 99.99% uptime.
Scenario 3: Security Tool Acquisition for Healthcare
A healthcare provider needs HIPAA-compliant vulnerability scanners. The Procurement Specialist:
- Selects Snyk for its HIPAA compliance certifications.
- Integrates it into Azure DevOps pipelines.
- Saves 20% by negotiating a multi-year contract.
Scenario 4: Outsourcing Penetration Testing
A tech startup requires regular pen-testing. The Procurement Specialist:
- Sources a third-party provider (e.g., Synopsys).
- Negotiates a $10,000 annual contract for quarterly tests.
- Ensures results feed into DevSecOps monitoring tools.
6. Benefits & Limitations
Key Advantages
- Cost Savings: Negotiates discounts, e.g., 15–30% on tool licenses.
- Compliance: Ensures tools meet regulatory standards (e.g., GDPR, HIPAA).
- Efficiency: Streamlines tool acquisition, reducing setup time.
- Vendor Relationships: Builds long-term partnerships for better SLAs.
Common Challenges or Limitations
- Complex Negotiations: Balancing cost, quality, and compliance can be time-consuming.
- Tool Integration: Lack of technical expertise may delay CI/CD integration.
- Vendor Lock-In: Long-term contracts may limit flexibility.
- Budget Constraints: High-cost DevSecOps tools may strain budgets.
7. Best Practices & Recommendations
Security Tips
- Verify vendor security certifications (e.g., ISO 27001).
- Include security clauses in contracts (e.g., data breach liability).
Performance
- Use analytics tools (e.g., Coupa Analytics) to track vendor performance.
- Monitor SLAs to ensure uptime and support quality.
Maintenance
- Regularly review vendor contracts for cost optimization.
- Update procurement policies to reflect new DevSecOps trends.
Compliance Alignment
- Align purchases with standards like NIST 800-53 or SOC 2.
- Use procurement platforms to document compliance.
Automation Ideas
- Automate RFQ processes using platforms like SAP Ariba.
- Integrate procurement data with CI/CD tools via APIs.
8. Comparison with Alternatives
Alternatives to Procurement Specialists
- In-House DevSecOps Team Sourcing: Developers or engineers directly select tools.
- Third-Party Procurement Services: Outsource procurement to firms like Accenture.
- Cloud Marketplaces: Use AWS Marketplace or Azure Marketplace for self-service procurement.
Comparison Table
| Aspect | Procurement Specialist | In-House Team | Third-Party Services | Cloud Marketplaces |
|---|---|---|---|---|
| Cost Efficiency | High (expert negotiation) | Moderate | High (fees apply) | Moderate |
| Compliance Expertise | High | Low | High | Moderate |
| Speed | Moderate | Fast | Slow | Very Fast |
| Customization | High | Moderate | High | Low |
When to Choose a Procurement Specialist
- Complex Needs: For large-scale, compliance-heavy projects.
- Cost Sensitivity: When budget optimization is critical.
- Long-Term Contracts: For negotiating multi-year vendor agreements.
9. Conclusion
Procurement Specialists are pivotal in enabling DevSecOps by sourcing secure, cost-effective, and compliant tools and services. Their role bridges technical and business needs, ensuring that DevSecOps pipelines are equipped with the right resources. As DevSecOps evolves, trends like AI-driven procurement, blockchain for supply chain transparency, and increased focus on ESG (Environmental, Social, Governance) will shape the role.