1. Introduction & Overview
What is Resource Allocation in DevSecOps?
Resource allocation in DevSecOps refers to the strategic assignment and management of computational, human, and security resources to optimize the software development lifecycle (SDLC) while ensuring security is integrated at every stage. This includes allocating compute resources (e.g., cloud instances, containers), human resources (e.g., developer and security team roles), and security tools (e.g., vulnerability scanners, monitoring systems) to balance speed, security, and efficiency in DevSecOps pipelines.
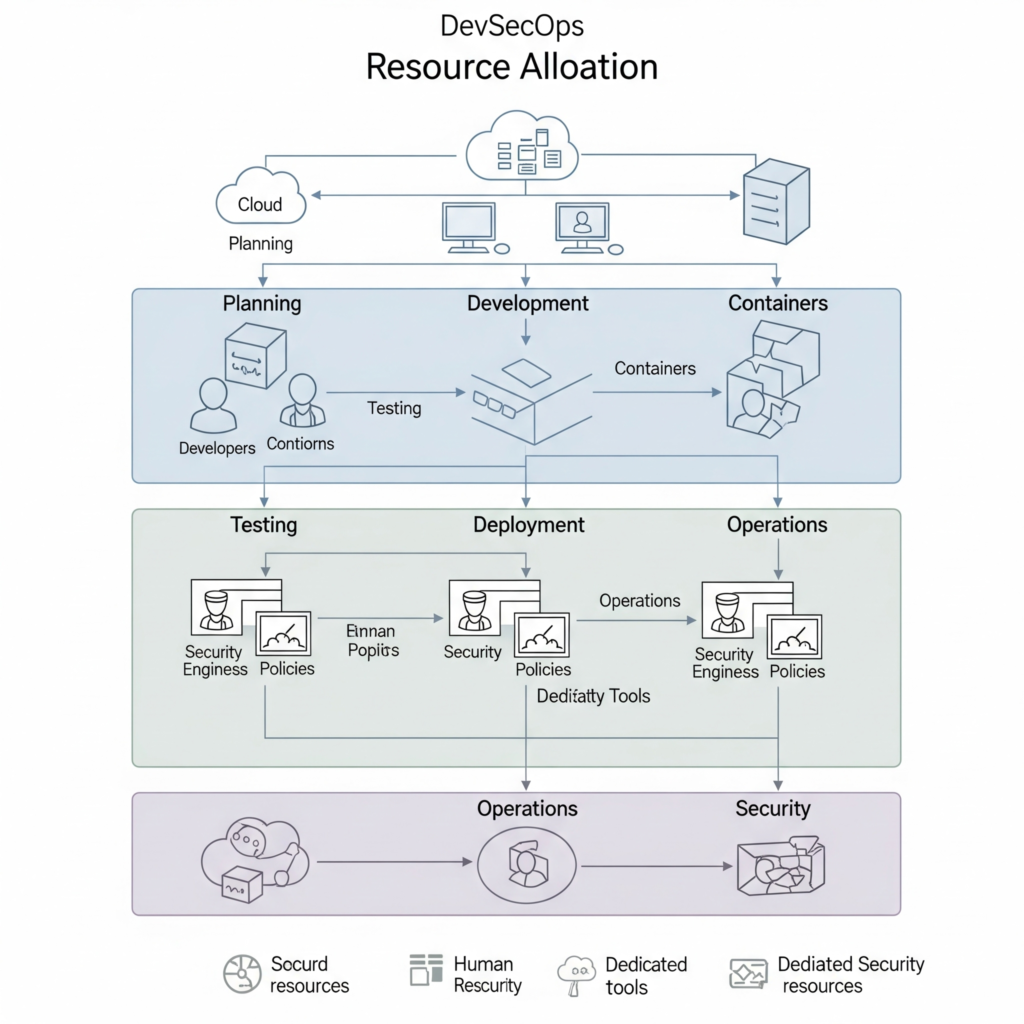
History or Background
The concept of resource allocation in software development evolved with the rise of DevOps in the early 2000s, which emphasized collaboration and automation to accelerate delivery. As security became a critical concern with faster release cycles, DevSecOps emerged around 2015, integrating security into DevOps workflows. Resource allocation became pivotal as organizations needed to manage limited resources (e.g., budget, compute power, skilled personnel) while addressing the “shift-left” security paradigm—embedding security early in the SDLC. Tools like Kubernetes, Terraform, and CI/CD platforms (e.g., Jenkins, GitLab) introduced automated resource allocation to scale infrastructure and security processes dynamically.
Why is it Relevant in DevSecOps?
Resource allocation is critical in DevSecOps for several reasons:
- Security Integration: Allocates security tools and personnel to ensure vulnerabilities are caught early without slowing development.
- Cost Efficiency: Optimizes cloud and infrastructure costs, crucial in dynamic environments like microservices or serverless architectures.
- Scalability: Ensures resources scale with project demands, supporting continuous integration/continuous deployment (CI/CD).
- Compliance: Aligns resource use with regulatory requirements (e.g., GDPR, HIPAA) by assigning security controls appropriately.
- Collaboration: Balances team workloads to foster cross-functional collaboration between development, security, and operations teams.
2. Core Concepts & Terminology
Key Terms and Definitions
- Resource Allocation: The process of assigning and managing resources (compute, human, tools) to achieve DevSecOps goals.
- Shift-Left Security: Integrating security practices early in the SDLC, requiring resource allocation for tools like SAST (Static Application Security Testing).
- CI/CD Pipeline: A workflow for continuous integration and deployment, where resources are allocated for automated builds, tests, and deployments.
- Infrastructure as Code (IaC): Managing infrastructure through code (e.g., Terraform), enabling automated resource allocation.
- Principle of Least Privilege (PoLP): Allocating minimal access to users, processes, or tools to reduce security risks.
- Observability: Monitoring resource usage and security performance using tools like Prometheus or Splunk.
| Term | Definition |
|---|---|
| Cost Allocation | Assigning cloud spend to specific services or teams. |
| Security Control Allocation | Mapping security practices (e.g., IAM, scanning) to owners. |
| Tagging/Labeling | Adding metadata to resources to enable traceable allocation. |
| Showback/Chargeback | Reporting or billing usage and costs back to the respective teams. |
| Shared Responsibility Model | Framework to define who is responsible for what across Dev, Sec, and Ops. |
How It Fits into the DevSecOps Lifecycle
Resource allocation spans the DevSecOps lifecycle (Plan, Code, Build, Test, Release, Deploy, Operate, Monitor):
- Plan: Allocate resources for threat modeling and security requirement definition.
- Code/Build: Assign compute resources for development environments and SAST tools.
- Test: Allocate testing tools (e.g., DAST, IAST) and environments for security validation.
- Release/Deploy: Use IaC tools to allocate infrastructure securely (e.g., Kubernetes clusters).
- Operate/Monitor: Allocate monitoring tools and incident response teams for runtime security.
[Plan] → [Code] → [Build] → [Test] → [Release] → [Deploy] → [Operate] → [Monitor]
↑ ↑ ↑
Cost Tags Risk Owners Security Control Owners
3. Architecture & How It Works
Components
- Compute Resources: Cloud instances, containers, or serverless functions allocated via platforms like AWS, Azure, or Kubernetes.
- Security Tools: Vulnerability scanners (e.g., Snyk, OWASP ZAP), monitoring tools (e.g., Splunk, Prometheus).
- Human Resources: Developers, security engineers, and operations teams assigned to specific tasks.
- CI/CD Tools: Jenkins, GitLab, or GitHub Actions for automating resource allocation in pipelines.
- Policy Management: Tools like OPA (Open Policy Agent) to enforce resource allocation policies.
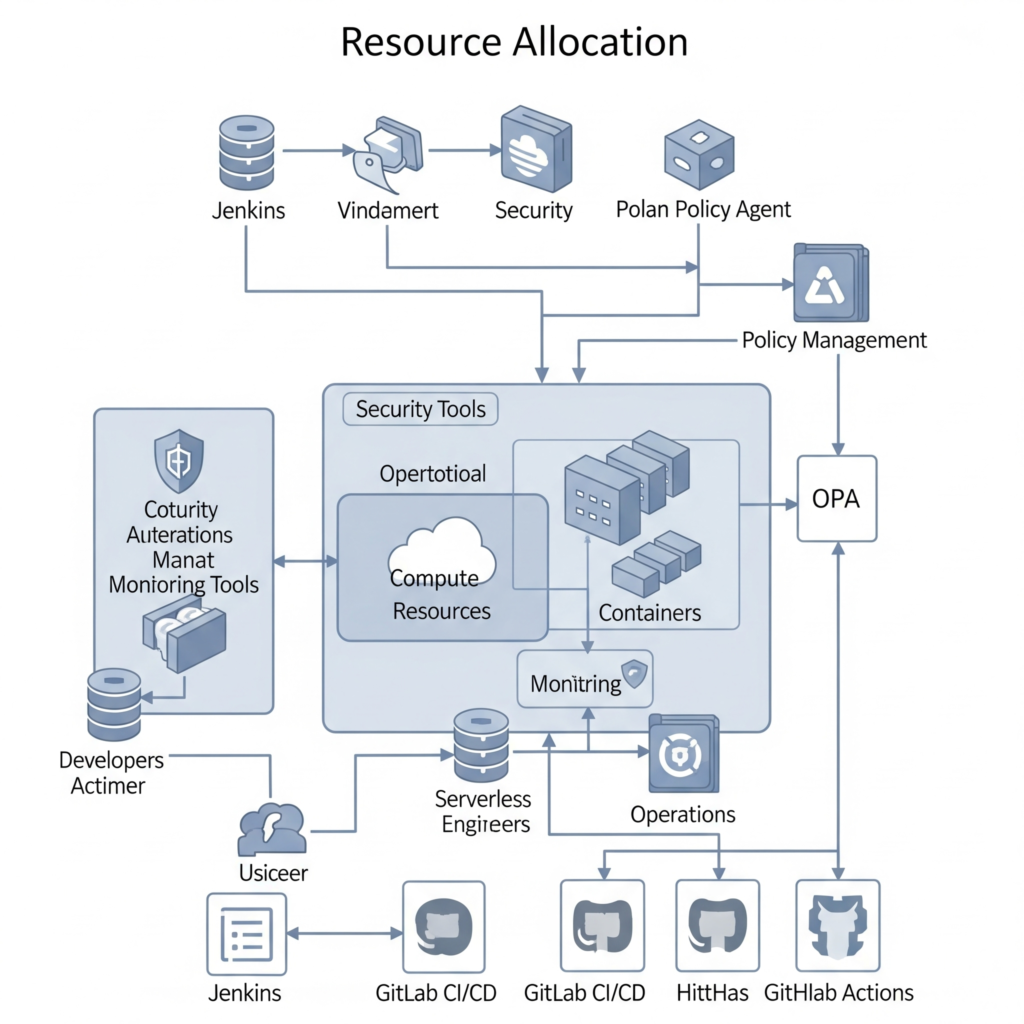
Internal Workflow
- Planning: Define resource needs (e.g., compute for test environments, tools for scanning).
- Allocation: Assign resources using IaC or orchestration tools (e.g., Kubernetes schedules pods based on resource requests).
- Execution: Resources are consumed during coding, building, testing, and deployment.
- Monitoring: Tools track resource usage and security metrics, adjusting allocations dynamically.
- Optimization: Reallocate resources based on feedback (e.g., scale down unused instances).
Architecture Diagram Description
Imagine a diagram with:
- Left: A CI/CD pipeline (Plan → Code → Build → Test → Deploy → Monitor).
- Center: Resource pools (cloud instances, containers, security tools, team roles).
- Right: Outputs (secure application, compliance reports, monitoring dashboards).
- Arrows show resources flowing from pools to pipeline stages, with feedback loops for optimization.
Developer Pushes Code
↓
CI/CD Pipeline Triggers
↓
Tagged Builds/Deployments (e.g., team:dev, app:api)
↓
Cloud Resources Provisioned with Labels
↓
Allocation Engine Aggregates Metrics (cost, risk, coverage)
↓
Dashboards / Alerts / Reports
Integration Points with CI/CD or Cloud Tools
- CI/CD Integration: Jenkins or GitLab allocates compute resources for builds and tests, integrating security tools like Snyk for vulnerability scanning.
- Cloud Integration: AWS CloudFormation or Terraform provisions infrastructure, while AWS WAF automates security policy allocation.
- Container Orchestration: Kubernetes uses resource quotas and namespaces to allocate compute and enforce PoLP.
4. Installation & Getting Started
Basic Setup or Prerequisites
- Cloud Account: AWS, Azure, or GCP account for infrastructure.
- CI/CD Tool: Jenkins, GitLab, or GitHub Actions installed.
- IaC Tool: Terraform or Ansible for infrastructure provisioning.
- Security Tools: Snyk, OWASP ZAP, or Checkmarx for scanning.
- Kubernetes: For containerized environments (optional).
- Skills: Basic knowledge of DevOps, cloud, and security principles.
Hands-On: Step-by-Step Setup Guide
This guide sets up a basic DevSecOps pipeline with resource allocation using Terraform and GitHub Actions.
- Install Terraform:
# On Ubuntu
sudo apt-get update && sudo apt-get install -y gnupg software-properties-common curl
curl -fsSL https://apt.releases.hashicorp.com/gpg | sudo apt-key add -
sudo apt-add-repository "deb [arch=amd64] https://apt.releases.hashicorp.com $(lsb_release -cs) main"
sudo apt-get update && sudo apt-get install terraform2. Set Up GitHub Actions:
- Create a
.github/workflows/devsecops.ymlfile in your repository:
name: DevSecOps Pipeline
on: [push]
jobs:
build:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v3
- name: Run Snyk to check for vulnerabilities
uses: snyk/actions@master
env:
SNYK_TOKEN: ${{ secrets.SNYK_TOKEN }}3. Configure Terraform for AWS:
- Create a
main.tffile to allocate an EC2 instance:
provider "aws" {
region = "us-east-1"
}
resource "aws_instance" "devsecops" {
ami = "ami-0c55b159cbfafe1f0"
instance_type = "t2.micro"
tags = {
Name = "DevSecOps-Instance"
}
}- Initialize and apply:
terraform init
terraform apply4. Integrate Security Scanning:
- Add Snyk to scan code in the pipeline:
snyk test --all-projects5. Monitor Resources:
- Use AWS CloudWatch or Prometheus to track instance usage and security alerts.
5. Real-World Use Cases
- Fintech: Secure Payment Processing
A fintech company allocates dedicated Kubernetes pods for payment microservices, using OPA to enforce PoLP and Snyk for dependency scanning. This ensures PCI DSS compliance and minimizes vulnerabilities. - Healthcare: Protecting Patient Data
A healthcare provider uses Terraform to allocate isolated AWS environments for HIPAA-compliant applications. Automated DAST tools (e.g., OWASP ZAP) scan APIs during CI/CD, reducing data breach risks. - E-commerce: Scalable Infrastructure
An e-commerce platform dynamically allocates cloud resources during peak sales using AWS Auto Scaling. Security tools like AWS WAF are allocated to protect against DDoS attacks. - Energy Sector: Legacy Modernization
An energy company allocates resources to migrate monolithic apps to microservices, using Ansible for configuration and Checkmarx for code security, improving release velocity and security.
6. Benefits & Limitations
Key Advantages
- Cost Optimization: Dynamic allocation reduces waste (e.g., scaling down unused instances).
- Enhanced Security: Early allocation of security tools reduces vulnerabilities.
- Scalability: Automated tools like Kubernetes handle resource spikes efficiently.
- Collaboration: Clear role allocation fosters Dev, Sec, and Ops teamwork.
- Compliance: Aligns resources with regulatory requirements (e.g., GDPR, HIPAA).
Common Challenges or Limitations
- Complexity: Managing diverse resources (cloud, tools, teams) can be overwhelming.
- Cost Overruns: Misallocated cloud resources can lead to high bills.
- Skill Gaps: Teams may lack expertise in IaC or security tools.
- Tool Integration: Incompatible tools can disrupt pipelines.
7. Best Practices & Recommendations
- Automate Allocation: Use IaC (Terraform, Ansible) to provision resources consistently.
- Enforce PoLP: Limit resource access using IAM roles and Kubernetes namespaces.
- Monitor Continuously: Use tools like Prometheus for real-time resource and security monitoring.
- Train Teams: Provide cross-functional training on security and DevOps tools.
- Compliance Alignment: Map resource allocation to standards like NIST 800-53 or ISO 27001.
- Optimize Pipelines: Integrate SAST/DAST tools early to catch issues without slowing CI/CD.
8. Comparison with Alternatives
| Aspect | Resource Allocation in DevSecOps | Manual Allocation | Static Allocation |
|---|---|---|---|
| Automation | High (IaC, CI/CD) | Low (manual setup) | Medium (predefined) |
| Security | Proactive (SAST, DAST) | Reactive | Limited |
| Scalability | Dynamic (Kubernetes, Auto Scaling) | Poor | Fixed |
| Cost Efficiency | High (optimized usage) | Low (overprovisioning) | Medium |
| Use Case | Agile, cloud-native projects | Small, legacy systems | Predictable workloads |
When to Choose Resource Allocation in DevSecOps:
- Choose for dynamic, cloud-based, or microservices projects requiring scalability and security.
- Avoid for small, static projects where manual allocation suffices.
9. Conclusion
Resource allocation in DevSecOps is a cornerstone of building secure, scalable, and efficient software delivery pipelines. By integrating compute, human, and security resources into every SDLC stage, organizations can achieve faster releases, robust security, and cost efficiency. Future trends include AI-driven allocation (e.g., predictive scaling) and zero-trust architectures for enhanced security. To get started, experiment with Terraform and Snyk in a small project, and explore communities like Practical DevSecOps (https://www.practical-devsecops.com) for resources.